Cloud-based WAF service “Scutum”

About Scutum
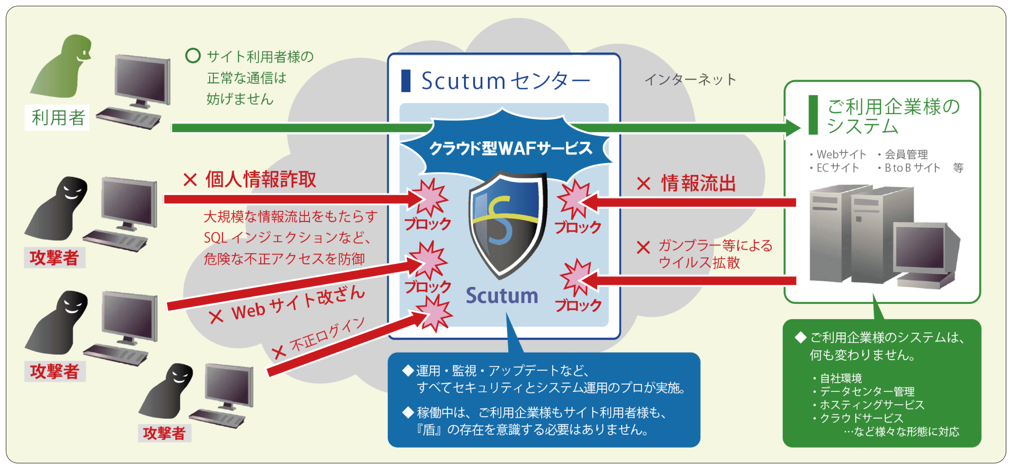
Scutum is a cloud-based (SaaS-based) web application firewall (WAF) service that protects customers from web application vulnerabilities such as SQL injection and cross-site scripting. It plays a role in protecting websites that generate dynamic pages in response to requests from unauthorized attacks.
Unlike general firewalls, it can analyze data content at the application level, so it provides flexible web application security for everything from small sites to cloud computing environments.
| Scutum service details | Scutum |
|---|
Features of Scutum
Cloud model (SaaS model) that changes the conventional wisdom of WAF
Conventional general WAF solutions are provided in the form of software embedded in hardware appliances and servers, and are assumed to be operated in-house. Maintaining WAF operations placed a heavy burden on engineers. In this way, although the concept of WAF itself is very good, the current situation is that it has not actually become very popular.
Scutum is cloud-based (SaaS) to overcome the issues associated with traditional WAFs, and provides web application firewall functionality via the Scutum Center.
In addition, you can complete the setup by simply changing the DNS settings so that the original IP address of your web server becomes the IP address of the Scutum service. It is possible to build a service environment.
Main security features
Communication to websites is relayed directly to the Scutum center by changing the DNS, and unauthorized communication is monitored and blocked in the process.
| 1 | block function | A function that blocks communications that appear to be attacks on websites. |
|---|---|---|
| 2 | Monitoring function | A function to record communications that appear to be attacks on websites (communications themselves are not blocked) |
| 3 | Defense log viewing function | A function that allows you to save and view blocked (monitored) communications as a log. |
| 4 | Report function | Function to report the following contents on the management screen - Top 5 attack sources (IP addresses) - Top 5 attack types - Monthly download of defense logs |
| 5 | Software update function | Ability to update software to improve defense effectiveness |
| 6 | Defense logic update function | A function that constantly updates unauthorized communication patterns to improve defense effectiveness. |
| 7 | Specific URL exclusion function | A function that excludes parts of a website that you do not want to use the WAF function from being protected. |
| 8 | IP address rejection/ permission setting function |
A function that rejects communication from a specific IP address or allows communication only from a specific IP address. |
| 9 | IP address management function for vulnerability inspection |
A function that does not block/monitor communications from the set IP address when performing vulnerability diagnosis on websites, etc. |
| 10 | SSL/TLS communication function | Function to decrypt and protect encrypted communications |
| 11 | API function | A function that allows you to obtain defense logs and detailed attack request contents detected by Scutum via API. |
Main attacks that can be defended against
Covers many of the major attacks against web application vulnerabilities. The defense logic is constantly updated to respond to new vulnerabilities, allowing customers to maintain the latest security measures without having to be particularly aware of them.
| Attack category | Attack name |
|---|---|
| certification | round robin |
| password list attack | |
| client side attack | cross-site scripting |
| CSRF (Cross Site Request Forgery) *Paid customization available |
|
| Execution with command | SQL injection |
| buffer overflow | |
| OS command injection | |
| XPath injection | |
| Format string attack | |
| LDAP injection | |
| SSI injection | |
| remote file inclusion | |
| Insecure deserialization (Java/PHP) | |
| Information disclosure | Directory indexing * Customization available for a fee |
| information leak | |
| path traversal | |
| Guess resource location | |
| Attack targeting XXE vulnerability | |
Attacks targeting specific middleware/ frameworks, etc. |
ShellShock attack |
| Attacks targeting Apache Struts2 vulnerabilities (OGNL injection, etc.) | |
| POODLE attack | |
| SSL BEAST attack | |
| HTTP request smuggling | |
| Spreading malware | Drive-by download attacks (virus spread by Gumblar, etc.) |
| Denial of service | DoS attacks that exploit platform vulnerabilities (ApacheKiller, hashDoS, etc.) |
| DoS attack from a small number of IP addresses (massive normal traffic, slowloris, SYN flood attack, etc.) | |
| DDoS attack from multiple IP addresses * Paid option available |
Administrator function list
Management functions can be easily and securely accessed via a web browser from the individual management screen on the subscriber-only page.
| 1 | WAF function control |
|---|---|
| 2 | Web server settings |
| 3 | IP address denial/permission settings |
| 4 | SSL/TLS settings (select SSL/TLS version/cipher suite to allow connection) |
| 5 | View log |
| 6 | SSL certificate renewal |
| 7 | Setting excluded URLs |
| 8 | change Password |
| 9 | E-mail address change |
| 10 | API key management |
| 11 | Capture function management *Optional support |