Cloud-based web application vulnerability diagnosis “VAddy”

About VAddy
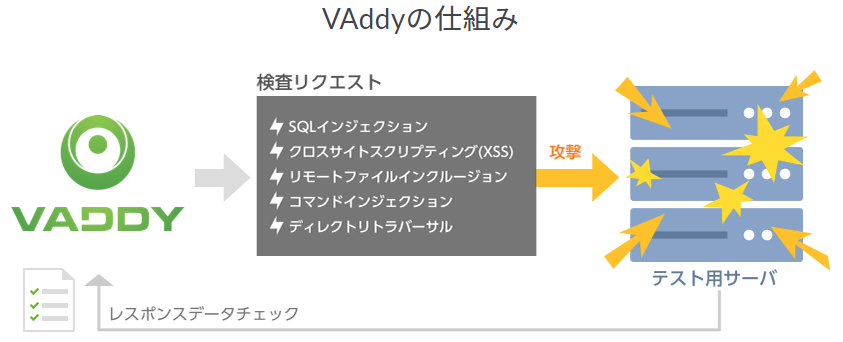
VAddy is a black box testing web vulnerability diagnosis service that allows developers to diagnose web application vulnerabilities themselves. Web application vulnerability diagnosis, which used to be performed at the final stage of development, can now be run as many times as you like from the early stages of development.
| VAddy service details | VAddy |
|---|
Features of VAddy
Start scanning in as little as 10 minutes after signing up
After registering the host to be inspected, simply record the URL and parameters of the screen you want to inspect in VAddy, and vulnerability diagnosis corresponding to realistic threats will be executed. Since it is possible to quickly inspect only parts of a web application where functions have been added or modified, vulnerability diagnosis can be completed in about 10 minutes each time, even for large-scale web applications. 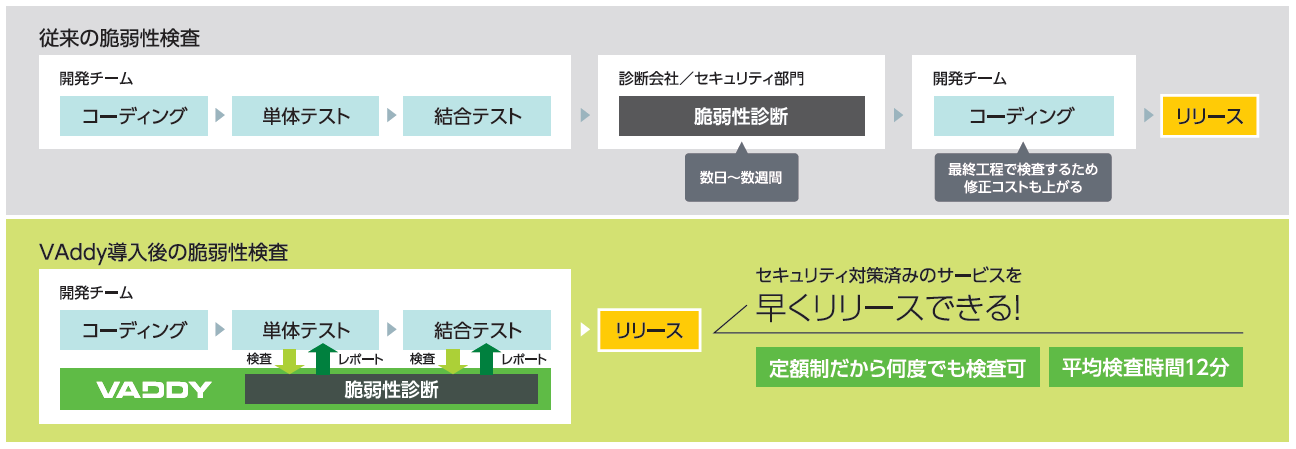
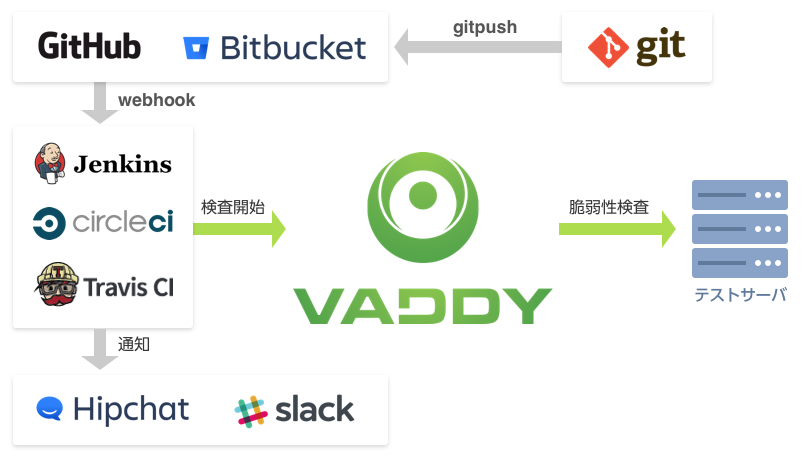
It is possible to build an automatic inspection environment that matches the environment, such as CI coordination and periodic execution.
We provide command tools to automate running vulnerability assessments and retrieving results. Using the WebAPI key provided by VAddy, you can freely construct an inspection environment that suits your development cycle, such as automatic execution of inspections in conjunction with CI (Continuous Integration), or daily regular execution using a shell. can do.
Main vulnerability diagnosis functions
| Inspection items for vulnerability diagnosis | ● Basic inspection items ・SQL injection ・Cross-site scripting (XSS) ・Remote file inclusion (RFI) ・Command injection ・Directory traversal ・ Blind SQL injection ・Insecure deserialization ・XML external entity attack (XXE) ・HTTP header injection ・SSRF Vulnerability /Private File Inspection●Optional Inspection Items ・Deficiencies in session management ・Cross-site request forgery (CSRF) ・E-mail header injection ・Clickjacking ・Buffer overflow ・Missing access control and authorization control |
|---|---|
| Main specifications/features | ・Japanese support ・Inspection report download (PDF) ・Number of scans: Unlimited ・Maximum scan time: 5 hours/time ・Scan history: Past 2 years ・Team function (number of members per project): Unlimited ・Organizational management function Members Number: 30 users / FQDN to be tested: 3FQDN / Diagnosis of local environment |
| External collaboration | ・CI cooperation ・Web API |