Cloud-based WAF service "Scutum"

About Scutum
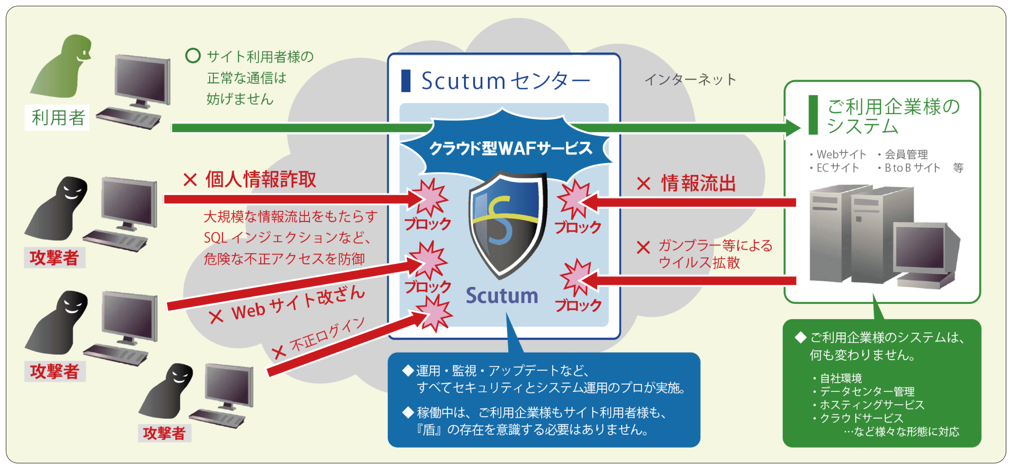
Scutum is a cloud-based (SaaS) web application firewall (WAF) service that protects customers from web application vulnerabilities such as SQL injection and cross-site scripting. It protects websites that generate dynamic pages in response to requests from malicious attacks
Unlike typical firewalls, it can analyze the contents of data at the application level, providing flexible web application security that can be adapted to everything from small sites to cloud computing environments
Features of Scutum
Cloud model (SaaS model) that changes conventional WAF concepts
Conventional WAF solutions are provided as software embedded in hardware appliance servers and are designed to be operated in-house, which places a heavy burden on engineers to maintain stable WAF operation, including the need to make complex configuration changes to servers and networks. As such, while the concept of WAF itself is excellent, it has not yet become widely adopted
Scutum is a cloud-based (SaaS) solution that overcomes the challenges associated with traditional WAFs, and provides web application firewall functionality via the Scutum Center
In addition, the setup can be completed simply by changing the DNS settings so that the IP address that your web server originally has becomes the IP address of the Scutum service, making it possible to build a more secure web service environment without having to own any additional equipment
Key security features
Communications to websites are relayed directly through the Scutum center by changing the DNS, and unauthorized communications are monitored and blocked during this process
| 1 | Blocking feature | A function to block communications that appear to be attacks against websites |
|---|---|---|
| 2 | Monitoring Function | A function to record communications that appear to be attacks against websites (the communications themselves are not blocked) |
| 3 | Defense log viewing function | A function that allows you to save and view blocked (monitored) communications as a log |
| 4 | Reporting | Ability to report the following information on the management screen: Top 5 attack sources (IP addresses) , Top 5 attack types , Monthly defense log downloads |
| 5 | Software update function | Ability to update software to improve defense effectiveness |
| 6 | Defense logic update function | A function that constantly updates malicious communication patterns to improve defense effectiveness |
| 7 | Specific URL exclusion function | A function that allows you to exclude parts of a website that you do not want to protect using the WAF function from the protection target |
| 8 | IP address rejection/ permission setting function |
A function to deny communication from specific IP addresses or to allow communication only from specific IP addresses |
| 9 | IP address management function for vulnerability testing |
A function that blocks/does not monitor communications from specified IP addresses when conducting vulnerability assessments on websites. |
| 10 | SSL/TLS communication function | Ability to decrypt and defend against encrypted communications |
| 11 | API Features | A function that allows you to obtain defense logs detected by Scutum and detailed attack request information via API |
Main attacks that can be defended against
It covers many of the major attacks against vulnerabilities in web applications. Since the defense logic is updated regularly to address new vulnerabilities, customers can maintain the latest security measures without any special effort on their part
| Attack Category | Attack Name |
|---|---|
| certification | Brute force |
| Password list attacks | |
| Client-side attacks | Cross-site scripting |
| CSRF (Cross-site request forgery) *Paid customization available |
|
| Execution by command | SQL injection |
| Buffer overflow | |
| OS Command Injection | |
| XPath Injection | |
| Format string attacks | |
| LDAP Injection | |
| SSI injection | |
| Remote File Inclusion | |
| Unsafe Deserialization (Java/PHP) | |
| Information Disclosure | Directory indexing * Customization available for a fee |
| Information leakage | |
| Path Traversal | |
| Guessing resource locations | |
| Attacks targeting XXE vulnerabilities | |
Attacks targeting specific middleware/ frameworks |
ShellShock attack |
| Attacks targeting vulnerabilities in Apache Struts2 (such as OGNL injection) | |
| POODLE attack | |
| SSL BEAST attack | |
| HTTP Request Smuggling | |
| Malware distribution | Drive-by download attacks (such as virus distribution by Gumblar) |
| Disruption of Service | DoS attacks that exploit platform vulnerabilities (ApacheKiller, hashDoS, etc.) |
| DoS attacks from a small number of IP addresses (massive normal traffic, Slowloris, SYN flood attacks, etc.) | |
| DDoS attacks from multiple IP addresses * Paid option available |
Administrator Function List
The management functions can be easily and securely accessed via a web browser from the individual management screen on the contracted user's page
| 1 | WAF function control |
|---|---|
| 2 | Configuring the Web Server |
| 3 | IP address rejection/permission settings |
| 4 | SSL/TLS settings (select the SSL/TLS version and cipher suite to allow connections) |
| 5 | Log Viewing |
| 6 | Renewing an SSL Certificate |
| 7 | Exclude URL settings |
| 8 | Change your password |
| 9 | Change your email address |
| 10 | Managing API keys |
| 11 | Capture function management *Optional |