A free and easy way for anyone to diagnose web content vulnerabilities

This is Ohara from the technical sales department.
This time's theme is "Web content vulnerability diagnosis."
As the blog title states,
we will introduce ``a free and easy way for anyone to diagnose vulnerabilities in web content''.
With any tool, you basically just enter the URL of the website you want to diagnose, so
it's really easy.
How to diagnose website vulnerabilities
■ gred
http://check.gred.jp/
This is a free version of "gred" provided by Secure Brain.
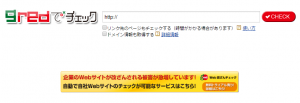 After entering the URL of the website in the form above and clicking the "CHECK" button, you
After entering the URL of the website in the form above and clicking the "CHECK" button, you
will be shown a result of the danger of the target web page after a short wait.
(If the website has many pages, it may take some time to judge.)
Unlike the paid version, some functions are limited, but
the feature is that you can also obtain linked pages and domain information.
■ Site Security Center
https://global.sitesafety.trendmicro.com/?cc=jp
This is a free website diagnostic service provided by Trend Micro.
to judge websites in four stages: safe, dangerous, suspicious, and unrated, and
even determine the category of the website.
Just like with gred above, if you enter the website URL in the form and
click the "Check now" button, you will receive the following judgment.
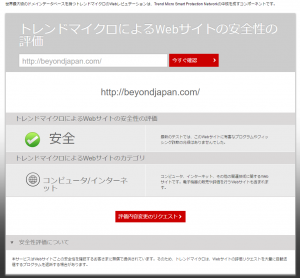
This time, I diagnosed it on Beyond's corporate website.
Of course, it is judged as a "safe" site, and it is judged in the "Computer/Internet" category.
By the way, newly created websites or
websites whose business content is difficult to discern from the content on the top page are likely to be marked as "not rated."
summary
It is predicted that attacks targeting vulnerabilities in websites and applications will continue to increase in intensity.
Although it is possible to understand the current status to some extent with the free vulnerability diagnosis introduced, we
still recommend installing a paid version of the security service to block attacks and detect tampering in real time
↓↓↓ [Click here for security services handled by Beyond] ↓↓↓
https://beyondjapan.com/option/deepsecurity
https://beyondjapan.com/option/waf
https://beyondjapan.com/option/gred

![[Osaka/Yokohama/Tokushima] Looking for infrastructure/server side engineers!](https://beyondjapan.com/cms/wp-content/uploads/2022/12/recruit_blog_banner-768x344.jpg)
![[Deployed by over 500 companies] AWS construction, operation, maintenance, and monitoring services](https://beyondjapan.com/cms/wp-content/uploads/2021/03/AWS_構築・運用保守-768x344.png)
![[Successor to CentOS] AlmaLinux OS server construction/migration service](https://beyondjapan.com/cms/wp-content/uploads/2023/08/almalinux_blogbanner-768x344.png)
![[For WordPress only] Cloud server “Web Speed”](https://beyondjapan.com/cms/wp-content/uploads/2022/11/webspeed_blog_banner-768x344.png)
![[Cheap] Website security automatic diagnosis “Quick Scanner”](https://beyondjapan.com/cms/wp-content/uploads/2023/04/quick_eyecatch_blogbanner-768x345.jpg)
![[Reservation system development] EDISONE customization development service](https://beyondjapan.com/cms/wp-content/uploads/2023/06/edisone_blog_banner-768x345.jpg)
![[Registration of 100 URLs is 0 yen] Website monitoring service “Appmill”](https://beyondjapan.com/cms/wp-content/uploads/2021/03/Appmill_ブログバナー-768x344.png)
![[Compatible with over 200 countries] Global eSIM “Beyond SIM”](https://beyondjapan.com/cms/wp-content/uploads/2024/05/beyond_esim_blog_slider1-768x345.jpg)
![[If you are traveling, business trip, or stationed in China] Chinese SIM service “Choco SIM”](https://beyondjapan.com/cms/wp-content/uploads/2024/05/china-sim_blogbanner-768x345.jpg)
![[Global exclusive service] Beyond's MSP in North America and China](https://beyondjapan.com/cms/wp-content/uploads/2024/06/gloval_surport_blog_slider-768x345.jpg)
![[YouTube] Beyond official channel “Biyomaru Channel”](https://beyondjapan.com/cms/wp-content/uploads/2021/07/バナー1-768x339.jpg)
 0
0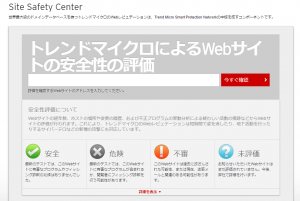

![[2025.6.30 Amazon Linux 2 support ended] Amazon Linux server migration solution](https://beyondjapan.com/cms/wp-content/uploads/2024/05/59b34db220409b6211b90ac6a7729303-1024x444.png)