[Radius] Testing Radius authentication via global (radtest)

table of contents
- 1 What you need
- 2 Building a local server with FreeRadius installed
- 3 Building an AWS server with FreeRadius and DaloRadius installed
- 4 Registering a RADIUS account
- 5 Change the client settings to allow authentication from the global IP address
- 6 Radius authentication from local server to AWS server
- 7 If Radius authentication fails
- 8 summary
- 9 lastly
Hello, this is Nagatani from the System Development Department.
In this article, I will introduce the procedure for verifying Radius authentication via global route using the radtest command.
To be honest, the method itself is quite simple and not particularly complicated, but when I searched online, I could only find instructions for local verification...
Also, it is highly unlikely that Radius authentication can be completed locally, and I wanted to conduct testing in a manner close to actual operation, so I decided to introduce it here
What you need
- A local server with FreeRadius installed
- AWS server with FreeRadius and DaloRadius installed
1 is a server that only allows you to use the radtest command.
To use the radtest command, you must have FreeRadius installed.
2 is a Radius server for verifying via global from the local server built in 1.
Since we want to create a Radius account, let’s install DaloRadius, which can manage accounts.
In this example, we are building a server on AWS, but you can use other platforms, so please use the one you prefer. The basic steps are the same
The idea is that 1 is the Radius client and 2 is the Radius server
Building a local server with FreeRadius installed
is clearly explained on
this site Also, since the purpose of this tutorial is to be able to use the radtest command, there is no need to configure the client or user.
Building an AWS server with FreeRadius and DaloRadius installed
Launch an EC2 instance on AWS and install FreeRadius and DaloRadius.
are clearly explained on this website
Registering a RADIUS account
Create a Radius account on the AWS server created above to verify Radius authentication
Log in to the DaloRadius admin page
Access the installed DaloRadius and log in.
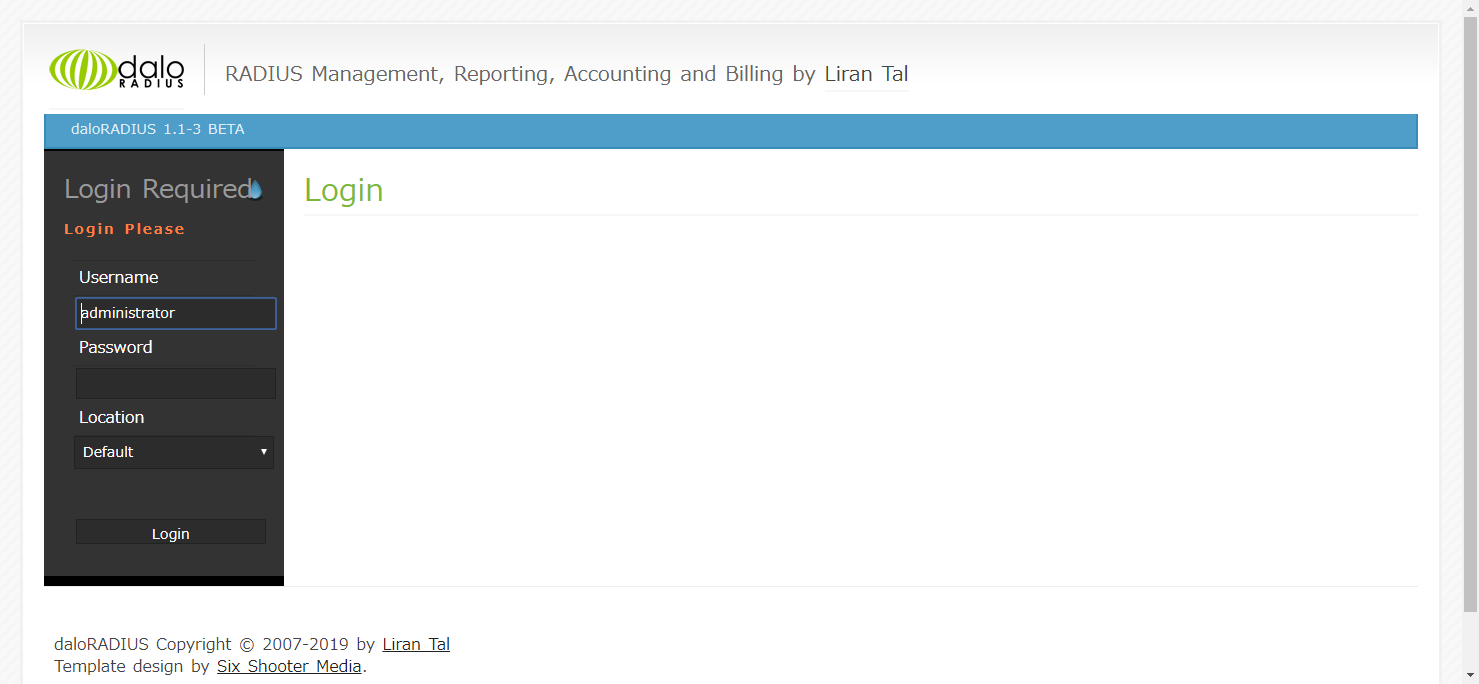
If you haven't made any changes, you can log in with Username:administrator, Password:radius.
Create an account
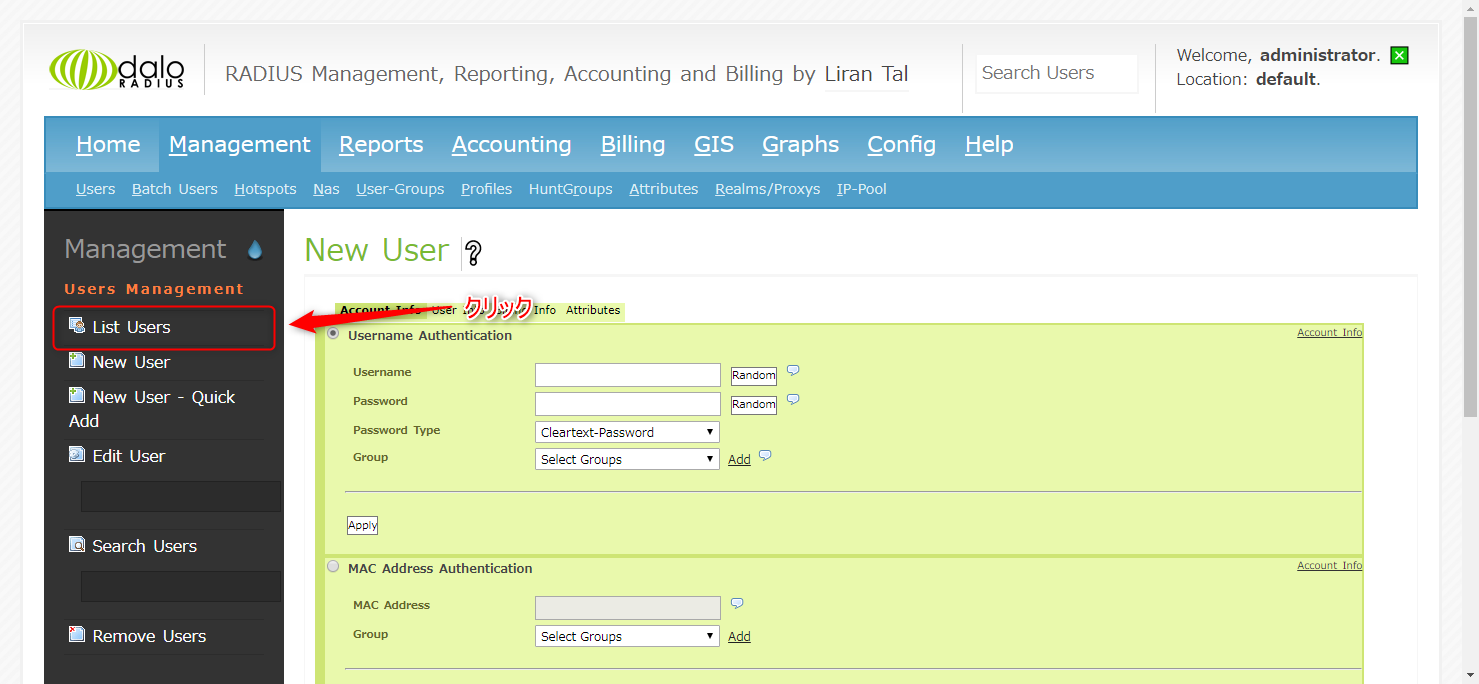
1. Select Management ⇒ New User
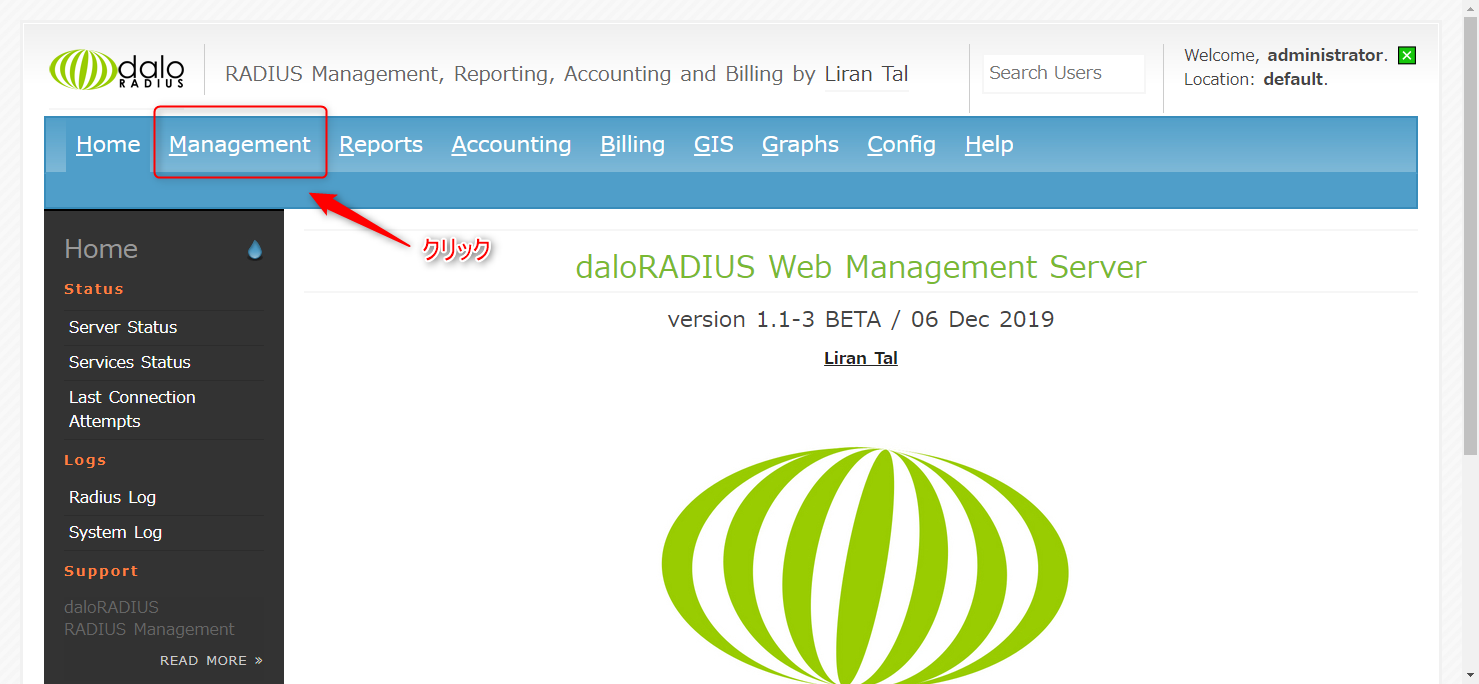
↓
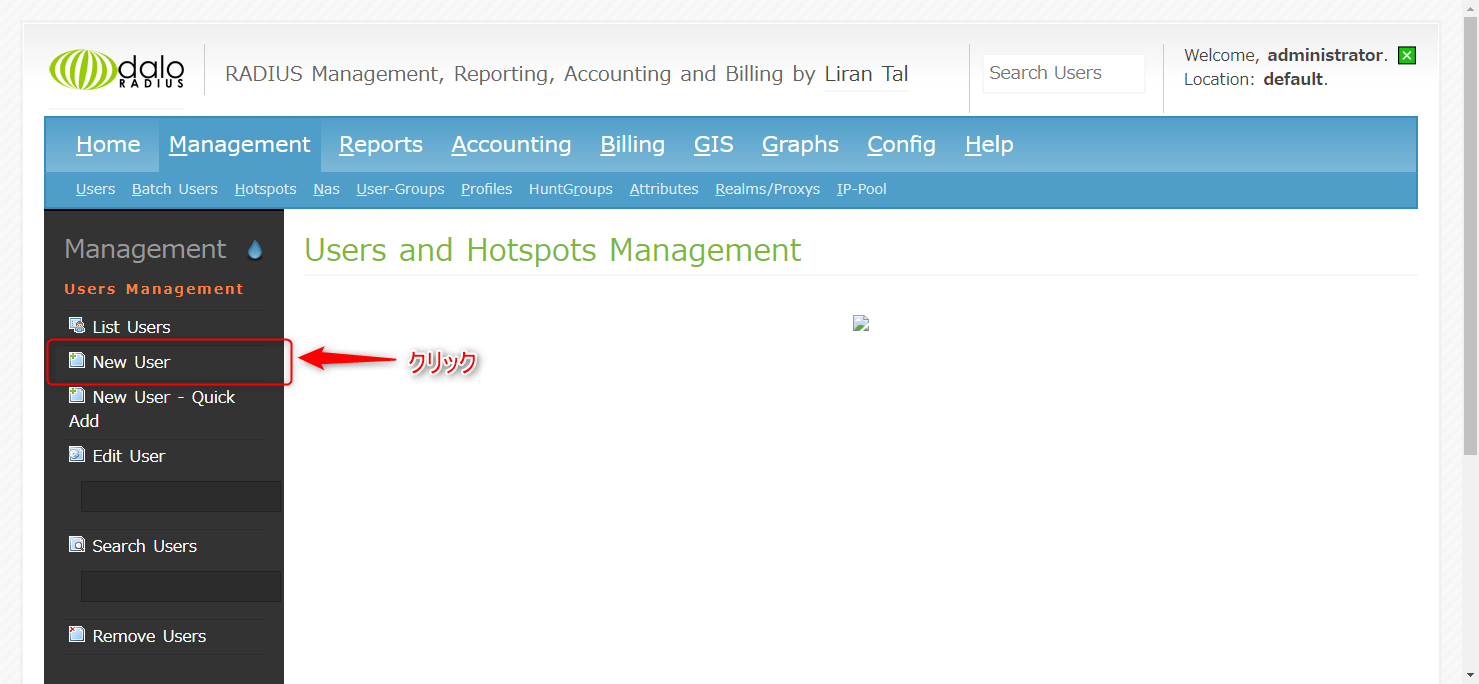
2. Enter your username and password in Username Authentication and click Apply
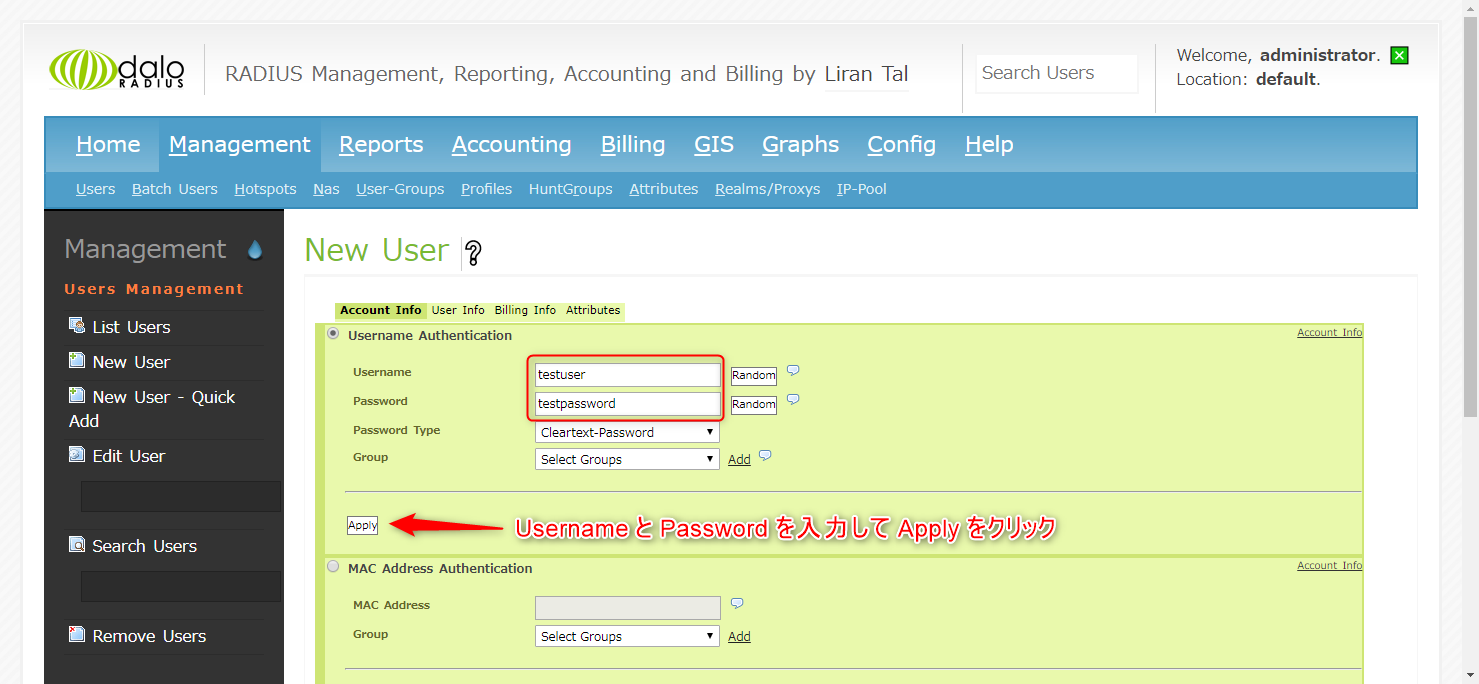
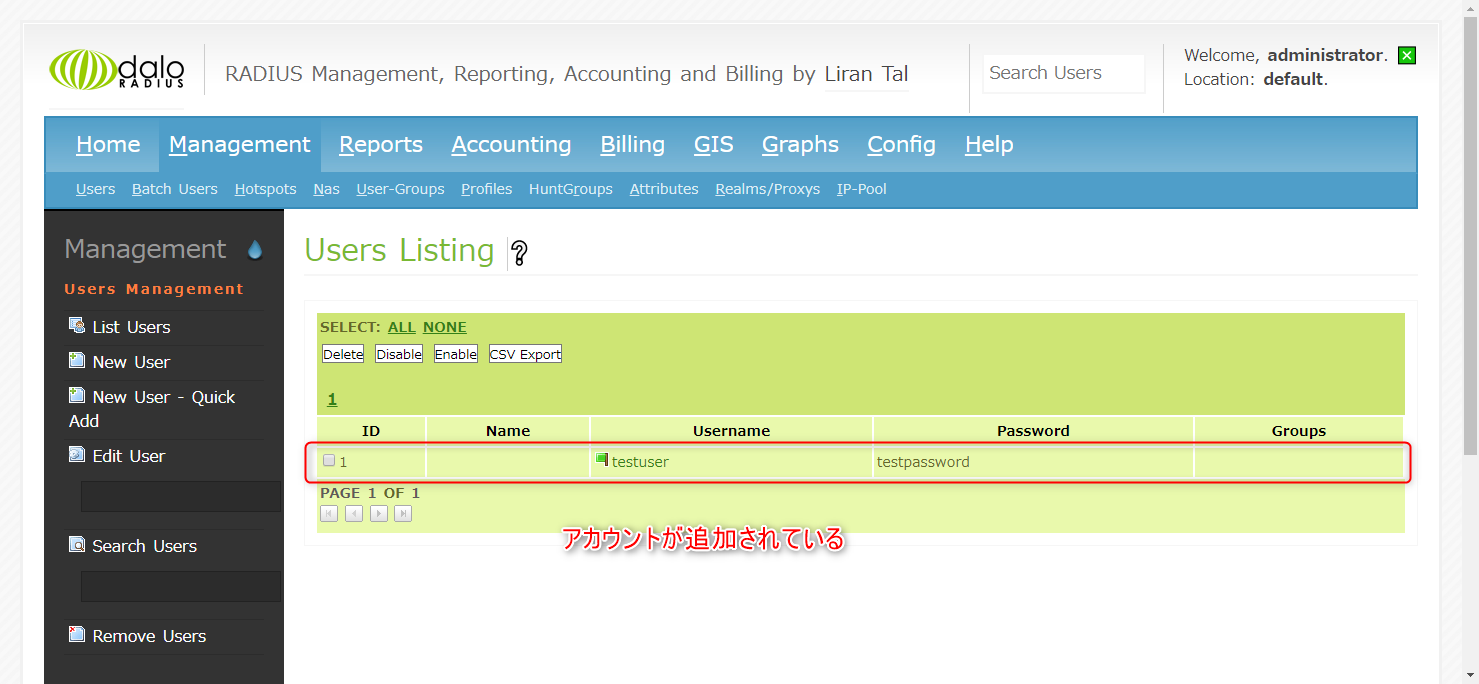
The account has now been created. In this example, it was created with testuser and testpassword.
You can also check the created account by clicking List Users.
↓
Change the client settings to allow authentication from the global IP address
Since we will be authenticating from a global client this time, add the following settings to clients.conf
client all { ipaddr = 0.0.0.0/0 secret = testing123 }
We are allowing authentication from all IP addresses with 0.0.0.0/0.
For the secret key, let's set it to testing123.
Now restart Radius and you're done.
Radius authentication from local server to AWS server
Now that we're ready, let's actually perform Radius authentication on the AWS server from the local server.
Run the following radtest command on the local server.
$ radtest testuser testpassword {AWS server IP} 1812 testing123
In terms of configuration,
radtest {username} {password} {AWS server IP} 1812 {secret key}
It will look something like this
If successful, Access-Accept will be returned as shown below
Sent Access-Request Id 43 from 0.0.0.0:48774 to {AWS server IP}:1812 length 78 User-Name = "testuser" User-Password = "testpassword" NAS-IP-Address = 127.0.0.1 NAS-Port = 1812 Message-Authenticator = 0x00 Cleartext-Password = "testpassword"
Now you have successfully authenticated via Radius globally
If Radius authentication fails
If there is no response when you run the above radtest and it times out as shown below
(0) No reply from server for ID 43 socket 3
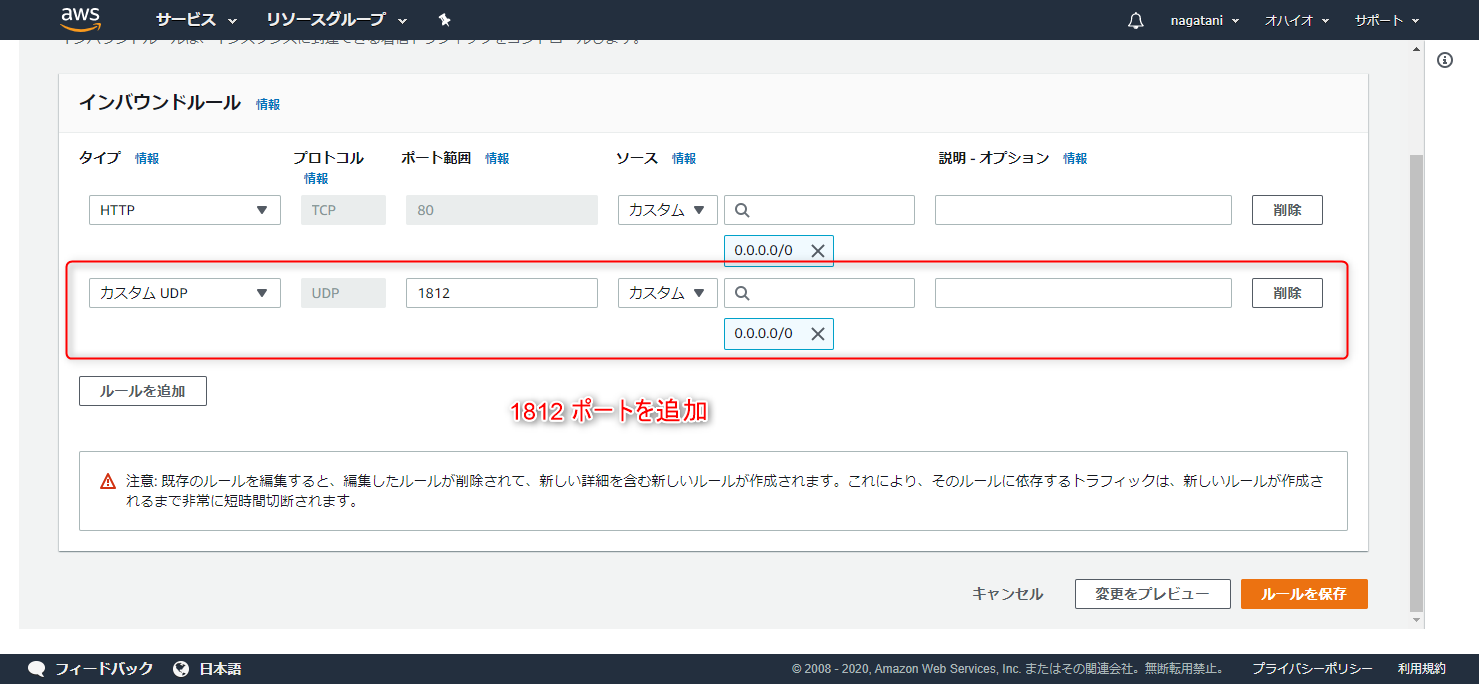
There may be access restrictions on port 1812 on the AWS server
Edit the inbound rules to add UDP on port 1812
summary
What do you think?
Well, it's basically the same as the normal local method, so I don't think it was that difficult.
However, I was surprised to find that this method wasn't listed anywhere, so I thought I'd introduce it this time.
I hope this is of some help to you
lastly
I am a member of the system development service site "SEKARAKU Lab."
Beyond offers a one-stop service for everything from server design and construction to operation, so if you have any problems with server-side development, please feel free to contact us.
SEKARAKU Lab: [https://sekarakulab.beyondjapan.com/](https://sekarakulab.beyondjapan.com/)
That's all.
Thank you very much!

 2
2






