About the features of server security “Trend Micro Security as a Service”

table of contents
This is Ohara from the technical sales department.
we will introduce the functions of "Trend Micro Security as a Service" that we handle
We also
provide technical support for ``Trend Micro Deep Security as a Service'', including license fees, initial settings, and security rule addition/operation
Main security features
The features of Deep Security as a Service are as follows.
- Anti-malware programs
- Web reputation
- firewall
- Intrusion detection and prevention
- change monitoring
- security log monitoring
Main features
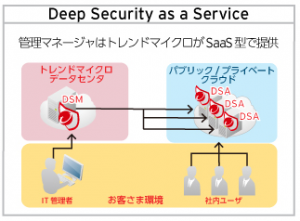
■ No need to build or operate a management server
With "Deep Security as a Service,"
Trend Micro provides a management server (DSM) in the cloud, so
there is no need to build a management server for implementation.
Users can log in to the management server provided by Trend Micro in the cloud and
easily change settings and manage logs.
This reduces the man-hours required to build a management server, and
allows you to quickly build and operate a highly secure system even when building a server in a short period of time using a public cloud.
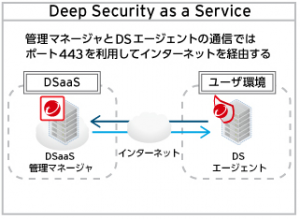
■ Internet connection to the target server to be protected
In the case of Deep Security as a Service,
the Admin Manager is hosted by Trend Micro, so
an Internet connection is required for the Admin Manager to communicate with your protected server.
■ Auto-scaling compatible
installed and preset security policies can be assigned
to cloud instances that increase or decrease with Auto-Scaling reducing the burden on operational administrators to configure settings each time.
*Additional licenses are also required when protecting temporarily increased instances using the Auto-Scaling function.
FAQ
Question : Is it possible to detect tampering with web content?
Answer : Tampering can be detected by specifying the tampering target.
*However, recovery of tampered web content is not covered.
Question : Is it possible to detect unauthorized access?
Answer : The firewall function allows you to block unauthorized communications.
Question : Is it possible to prevent communication and execution of illegal SQL statements and OS commands? (SQL injection, etc.)
Answer
It is possible to block and detect attacks for which Trend Micro has established rules for SQL commands as "exploit codes."
[Exploit code]
● A program that uses security holes to reproduce the behavior of unauthorized operations.
Question : Is it possible to detect and prevent unauthorized logins?
Answer : Brute force attacks are detectable.
It does not support attacks such as password list attacks.
[Password list attack]
● This is an attack that attempts to mechanically gain access using a legitimate account and password.
Question : Is it possible to keep logs of unauthorized access?
Answer : Firewall, IPS/IDS, and Integrity Monitoring log storage is possible.
Question : Is it possible to issue an alert for virus intrusion?
Answer : You can send a notification email to the administrator when a virus is detected.
Even if you have specified a target range using the change monitoring function, or if an unknown file is installed,
it is possible to notify you after detection.
Additionally, attacks with security holes
can be monitored, blocked, and notified using the corresponding virtual patch (signature).
Question : Is it possible to store DeepSecurity operating status logs? (Operating status monitoring and reporting function)
Answer : Information such as CPU and memory load rates
is uploaded to DSM (DeepSecurity management server) on a host-by-host basis. This information can also be exported at any time.
summary
These are the characteristics of "Deep Security as a Service".
It is recommended for users who want to increase the security of their web service servers because it is equipped with flexible functions such as automatic installation with AWS Auto-Scaling.
Also, if you want to strengthen security at the web application level,
it would be a good idea to introduce a cloud-based WAF in addition to this "Deep Security as a Service".
If you are looking for a cloud-based WAF, we recommend SecureSky Technology 's "Scutum."

![[Osaka/Yokohama/Tokushima] Looking for infrastructure/server side engineers!](https://beyondjapan.com/cms/wp-content/uploads/2022/12/recruit_blog_banner-768x344.jpg)
![[Deployed by over 500 companies] AWS construction, operation, maintenance, and monitoring services](https://beyondjapan.com/cms/wp-content/uploads/2021/03/AWS_構築・運用保守-768x344.png)
![[Successor to CentOS] AlmaLinux OS server construction/migration service](https://beyondjapan.com/cms/wp-content/uploads/2023/08/almalinux_blogbanner-768x344.png)
![[For WordPress only] Cloud server “Web Speed”](https://beyondjapan.com/cms/wp-content/uploads/2022/11/webspeed_blog_banner-768x344.png)
![[Cheap] Website security automatic diagnosis “Quick Scanner”](https://beyondjapan.com/cms/wp-content/uploads/2023/04/quick_eyecatch_blogbanner-768x345.jpg)
![[Reservation system development] EDISONE customization development service](https://beyondjapan.com/cms/wp-content/uploads/2023/06/edisone_blog_banner-768x345.jpg)
![[Registration of 100 URLs is 0 yen] Website monitoring service “Appmill”](https://beyondjapan.com/cms/wp-content/uploads/2021/03/Appmill_ブログバナー-768x344.png)
![[Compatible with over 200 countries] Global eSIM “Beyond SIM”](https://beyondjapan.com/cms/wp-content/uploads/2024/05/beyond_esim_blog_slider1-768x345.jpg)
![[If you are traveling, business trip, or stationed in China] Chinese SIM service “Choco SIM”](https://beyondjapan.com/cms/wp-content/uploads/2024/05/china-sim_blogbanner-768x345.jpg)
![[Global exclusive service] Beyond's MSP in North America and China](https://beyondjapan.com/cms/wp-content/uploads/2024/06/gloval_surport_blog_slider-768x345.jpg)
![[YouTube] Beyond official channel “Biyomaru Channel”](https://beyondjapan.com/cms/wp-content/uploads/2021/07/バナー1-768x339.jpg)
 0
0![[2025.6.30 Amazon Linux 2 support ended] Amazon Linux server migration solution](https://beyondjapan.com/cms/wp-content/uploads/2024/05/59b34db220409b6211b90ac6a7729303-1024x444.png)