Merry Christmas。∠(*・m・)v Do you know about Christmas Scan?

table of contents
Hello,
I'm Kawa from the System Solutions Department.
The end of the year has flown by so quickly.
It's already dark and cold outside at 5pm, so I just want to stay warm and cozy in my kotatsu and play Switch all day.
December is the month of Christmas.
It's been a long time since Santa came to visit me,
but it's nice to see the streets sparkling with color. ∠(*・m・)v
As the title suggests, there is something Christmas-related in IT as well.
Have you heard of "Christmas (tree) scan"?
It's the name of a network attack, and techies have coined a number of terms for it, which is quite amusing
(though actually being attacked isn't so funny),
so I thought I'd write a bit about this Christmas scan today.
What is Christmas Scan?
It's known by various names, such as Christmas scan or Christmas tree attack, and
it comes from the control flags in the packets.
generally use stealth scans as a port scan method to avoid being caught,
Packets (we're talking about TCP in this case) have a 6-bit section called control flags,
which are used to control the connection. ACK and SYN are well-known.
The Christmas scan uses the following three of them:
URG (Urgent) - Contains data that needs to be processed urgently (priority)
PSH (Push) - Pass data immediately to the upper level without buffering
RST (Reset) - Forcefully terminates the connection
Other than RST, these flags may be unfamiliar to you.
Christmas Scan is an attack method that sets the bits of these three flags to "1" and
sends them as the first packet to check the target's reaction.
Why Christmas?
As mentioned above, this is because there are three flags set, but it doesn't really make sense, does it?
Actually, you need to capture packets and visualize them using Wireshark or similar, but
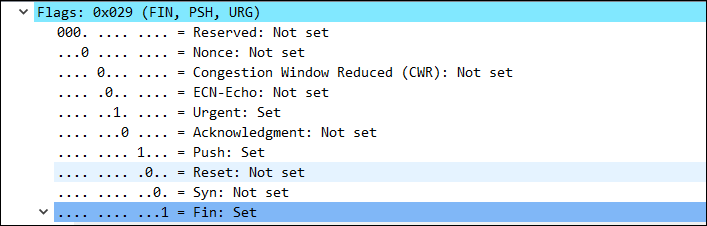
the flags are colorful. In addition, the flag structure is cone-shaped, like the right half of the tree, so
it looks like the tree is colored, which is apparently why it's called that.
⬇It

doesn't look like this very often.
Why is this an attack?
It's more of a port scan than an attack, so more accurately it can be called "preparation for an attack."
As you know, TCP packets follow a three-way handshake sequence: SYN-ACK-FIN.
But what happens if an out-of-state packet comes along that ignores this sequence?
If the port is open,
the behavior will differ depending on the OS, but since it is not a SYN or anything like that, if the port is open, it
means that a third party can easily tell that the port is open
If the port is not open
, the sender will receive a RST packet,
but the port will be closed.
By the way, Windows specifications seem to respond with an RST regardless of whether the port is open or closed, so
there is a possibility that the OS may be revealed.
Also, the behavior of firewalls and UTMs may change depending on whether they throw an RST or not, so
there is a risk that open ports may be revealed depending on the combination with other attacks.
complete

 13
13






