[China] Alibaba Cloud's WAF function [Security]
![]()
table of contents
This is Ohara from the Technical Sales Department
This article describes the features and functions of
Alibaba Cloud WAF a WAF service provided by Alibaba Cloud *This information is current as of September 2021.
Alibaba Cloud Security History
Alibaba Cloud is focusing on developing security products to protect Alibaba Cloud services from various external cyber attacks
One of these security products, Alibaba Cloud WAF (Web Application Firewall), is a service for defending against web attacks developed based on Alibaba Cloud's more than 10 years of security experience. It is an evolved service equipped with advanced defense mechanisms that utilize big data capabilities
Alibaba Cloud WAF Service Overview
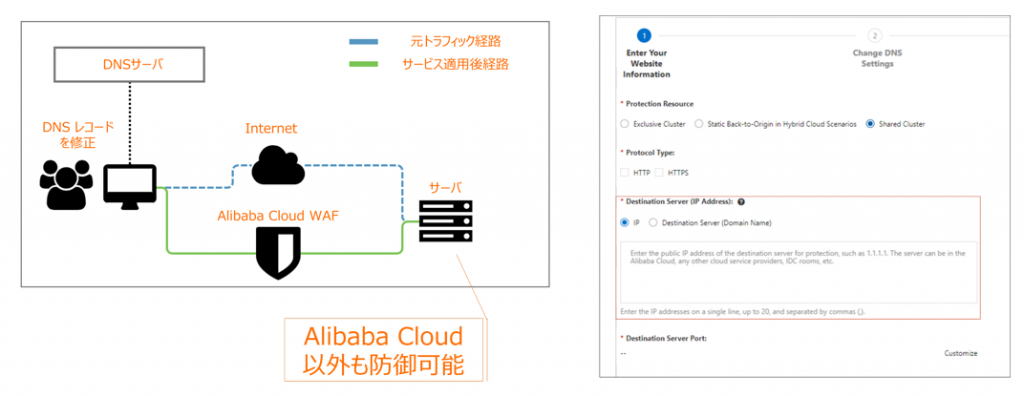
Alibaba Cloud WAF can be installed not only on Alibaba Cloud, but also on systems running on-premise, VPS, or other companies' cloud servers simply by switching DNS, making it suitable for any infrastructure environment
■ Web application protection
● Zero-day attack protection
: Dynamically updating defense rules within 24 hours allows for rapid response to risks.
● Website concealment
: Using DNS to divert traffic hides and protects your site from intruders.
● OWASP attack protection
: Provides a variety of defense policies and quarantine functions, accurately identifying and defending against known attacks such as SQL injection.
■ Site access control
● Adding HTTPS functionality:
Simply upload a private key file to add HTTPS functionality to your site.
● Access control
: Multi-layer protection identifies and blocks information gathering attempts on your site that may be necessary for intrusion.
■ Highly accurate traffic analysis
● Accurate malicious access judgment
- Malicious access such as bots can be accurately identified and evaluated before being blocked.
● Custom policy
- Defense rules can be freely changed and reflected as needed.
Alibaba Cloud WAF Features (by Edition)
Alibaba Cloud WAF offers four editions to choose from depending on processing power, defense functions, and use cases.
For example, you can start small with the Professional edition and change editions as web access increases, allowing you to flexibly scale up according to your needs and circumstances.
| Features | overview | Pro Edition | Business Edition | Enterprise Edition | Exclusive Edition (submit tickets to purchase) |
| Peak Request Rate | - | 2,000 QPS | 5,000 QPS | Higher than 10,000 QPS | 5,000 QPS |
| Maximum Bandwidth | If your origin server is deployed on Alibaba Cloud | 50 Mbit/s | 100 Mbit/s | 200 Mbit/s | 100 Mbit/s |
| If your origin server is not deployed on Alibaba Cloud | 10 Mbit/s | 30 Mbit/s | 50 Mbit/s | 30 Mbit/s | |
| Maximum number of domains supported by default | - | 1 | 1 | 1 | 1,000 |
| Maximum number of subdomains supported by default | Wildcard domain support | 10 | 10 | 10 | 1,000 |
| HTTPS protection | Implement HTTPS protection for your website in just a few clicks | ✓ | ✓ | ✓ | ✓ |
| HTTPS/2 protection | Secure websites that use HTTP/2 | × | ✓ | ✓ | ✓ |
| Non-standard port protection | Protects traffic over ports other than the standard ports 80, 8080, 443, and 8443 | × | ✓ | ✓ | ✓ |
| Intelligent Load Balancing | Connect multiple SLB service nodes for automatic disaster recovery and optimal routing with low latency | ○ | ○ | ○ | ○ |
| Exclusive IP Address | Provides exclusive IP addresses to protect specific domain names | ○ | ○ | ○ | ○ |
| Exclusive Cluster | Customize service access and protection features based on your business requirements | × | × | × | ✓ |
| Protection Rules Engine | Protects against common web attacks such as SQL injection and XSS attacks | ✓ | ✓ | ✓ | ✓ |
| Enable automatic updates for protection rules against zero-day web vulnerabilities | ✓ | ✓ | ✓ | ✓ | |
| Custom Protection Rule Groups | Customize protection rule groups | × | ✓ | ✓ | ✓ |
| Big Data Deep Learning Engine | Detect zero-day web vulnerabilities | × | ✓ | ✓ | ✓ |
| Positive Security Model | Proactive defense based on deep learning of website traffic | × | × | ✓ | ✓ |
| Prevent website tampering | Lock web pages to prevent content tampering | ✓ | ✓ | ✓ | ✓ |
| Data Leak Prevention | Prevents leakage of confidential data such as ID card numbers, mobile phone numbers, and bank card numbers | ✓ | ✓ | ✓ | ✓ |
| HTTP Flood Protection | Protects against common HTTP flood attacks in preventative or preventative emergency modes | ✓ | ✓ | ✓ | ✓ |
| Blacklist | Block access requests from specific IP addresses or CIDR blocks | ✓ | ✓ | ✓ | ✓ |
| Block access requests from specific IP addresses, specific CIDR blocks, or IP addresses in specific regions | × | ✓ | ✓ | ✓ | |
| Scan Protection | Block IP addresses from which web attacks and path traversals are frequently launched, as well as IP addresses of scanning tools, to provide a coordinated defense (default rules are used to block the first type of IP addresses) | ✓ | ✓ | ✓ | ✓ |
| Supports the above protection features and customizes blocking rules for common web attacks and path traversal | × | ✓ | ✓ | ✓ | |
| Custom Protection Policies | Supports ACL-based access control using basic fields such as IP, URL, referrer, user agent, and parameters | ✓ | ✓ | ✓ | ✓ |
| Supports ACL-based access control using basic and advanced fields (Advanced fields include Cookie, Content-Type, Header, and HTTP-Method) | × | ✓ | ✓ | ✓ | |
| Configure rate limiting policies based on IP addresses and sessions (customize HTTP flood protection rules that allow you to add match conditions and configure rate limiting policies) | × | ✓ | ✓ | ✓ | |
| Configure rate limiting policies based on IP addresses, sessions, and custom fields | × | × | ✓ | ✓ | |
| Data Risk Management | Protects important website services like registration, log-on, activity, and forums from fraud | ○ | ○ | ○ | ○ |
| Allowed crawlers | Maintaining a whitelist of approved search engines, such as Google, Bing, Baidu, and Yandex (these search engines' crawlers have access to the specified domain names) | ○ | ○ | ○ | ○ |
| Bot Threat Intelligence | Providing information about suspicious IP addresses used by data centers and malicious scanners (we also maintain a library of malicious crawler IP addresses and prevent crawlers from accessing all pages under a domain name or specific directories) | ○ | ○ | ○ | ○ |
| App Protection | Provides secure connections and anti-bot protection for native apps (identifies requests from proxy servers and emulators, as well as requests with invalid signatures) | ○ | ○ | ○ | ○ |
| Account Security | Detects dictionary attacks, brute force attacks, spam user registrations, weak passwords, and SMS flood attacks against service endpoints such as registration endpoints and logon endpoints | ✓ | ✓ | ✓ | ✓ |
| WAF log service | Collects and stores all logs, enabling near real-time querying and analysis, and providing online reports | × | ○ | ○ | ○ |
summary
Alibaba Cloud WAF is a SaaS solution, so it can be used in on-premise and cloud infrastructure environments other than Alibaba Cloud. Its multi-cloud compatibility makes it highly versatile

 0
0