[AWS IAM] Policy settings that allow access to only specific hosted zones
table of contents
- 1 overview
- 2 How to set it up
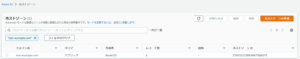
- 2.1 ①Copy the Hosted Zone ID of the corresponding domain name in Route53>Hosted Zones
- 2.2 ②IAM>Policies>【Create Policy】
- 2.3 ③Create a policy>Enter the information in the JSON tab and click [Next step: Tags]
- 2.4 ④Specify the following and click [Next Step: Confirm]
- 2.5 ⑤ Confirm the policy and click [Create Policy]
- 2.6 ⑥ Attach the created policy to the user
- 2.7 ⑦Log in and check operation
- 3 summary
Hello!
I'm Hide, the Ramen King from Beyond Inc.'s Osaka office.
This is my 12th post.
Last time, I wrote about how to display a WordPress site displayed in a subdirectory on the homepage!
The change is relatively easy, but if you make a mistake in the settings, you may encounter problems such as a blank screen.
I also introduced a solution to that problem, so if you're interested, be sure to check it out.
overview

"I want to create a user that can only view this hosted zone...
how do I do that...?"
Have you ever found yourself in the situation described above? Perhaps
you want another company to check a specific hosted zone, but
you don't know how to adjust permissions to allow them to view it only.
I also looked into this using information from AWS references and other articles, but it took quite a while...
However, if you look at this, you can easily set permissions, so let's take a look together!
How to set it up
①Copy the Hosted Zone ID of the corresponding domain name in Route53>Hosted Zones
②IAM>Policies>【Create Policy】
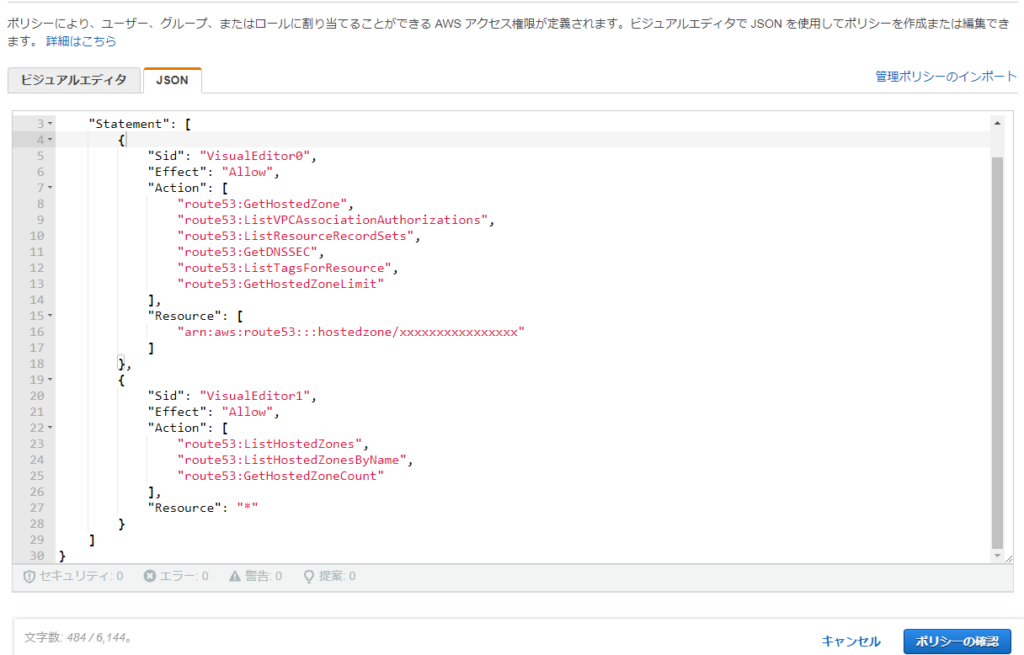
③Create a policy>Enter the information in the JSON tab and click [Next step: Tags]
* arn:aws:route53:::hostedzone/ Please enter the hosted zone ID in the xxxxxxxxxxxxxxxxxx
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "route53:GetHostedZone", "route53:ListVPCAssociationAuthorizations", "route53:ListResourceRecordSets", "route53:GetDNSSEC", "route53:ListTagsForResource", "route53:GetHostedZoneLimit" ], "Resource": [ "arn:aws:route53:::hostedzone/xxxxxxxxxxxxxxxxxx" ] }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": [ "route53:ListHostedZones", "route53:ListHostedZonesByName", "route53:GetHostedZoneCount" ], "Resource": "*" } ] }
| Action List | |
| Action Name | explanation |
| GetHostedZone | Grants permission to retrieve information about the specified hosted zone, including the four name servers that Route 53 has assigned to the hosted zone |
| ListVPCAssociationAuthorizations | Grants permission to retrieve a list of VPCs created by other accounts that can be associated with the specified hosted zone |
| ListResourceRecordSets | Grants permission to list the records in the specified hosted zone |
| GetDNSSEC | Grants permission to retrieve information about DNSSEC for a specific hosted zone, including the hosted zone's key-signing key |
| ListTagsForResource | Grants permission to list tags for a single health check or hosted zone |
| GetHostedZoneLimit | Grants permission to get the specified limit for the specified hosted zone |
| ListHostedZones | Grants permission to retrieve a list of public and private hosted zones associated with the current AWS account |
| ListHostedZonesByName | Gives permission to retrieve the list of hosted zones in lexicographical order. Hosted zones are sorted by reversed label name (e.g. com.example.www |
| GetHostedZoneCount | Grants permission to retrieve the number of hosted zones associated with the current AWS account |
| Resource types list | |
| Resource type name | explanation |
| hostedzone | You can restrict actions by specifying a hosted zone ID |
④Specify the following and click [Next Step: Confirm]
Key: Name
Policy: *Please specify your preferred name
⑤ Confirm the policy and click [Create Policy]
Name: Please specify your preferred name
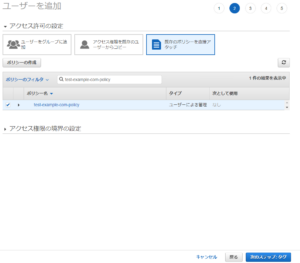
⑥ Attach the created policy to the user
⑦Log in and check operation
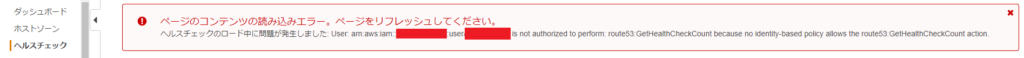
*If you try to check something other than the hosted zone, such as a health check, the following error will occur:
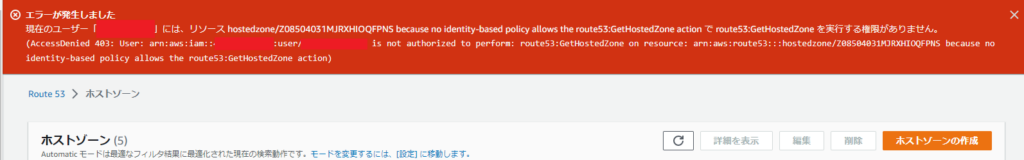
*Due to the permission specifications, you can only see the list of other hosted zones in the hosted zone list, but when you try to check the contents, the following error occurs
・Hosted Zone List Screen
・Error screen
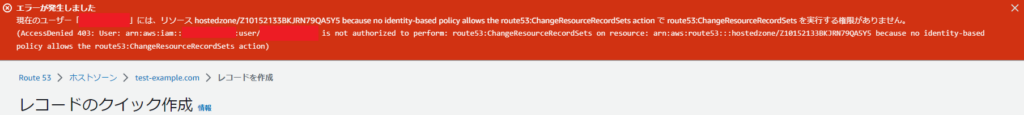
*When I try to create, delete, or edit a record, the following error occurs:
summary
What did you think?
Because policy settings allow you to set permissions in great detail, there are probably many things you won't understand even if you look at the official reference.
I also found it difficult to understand and had a lot of trouble...
However, if you use this procedure, you can easily create a policy that allows you to view a specific hosted zone,
so if you ever need it, please take a look!
Thank you for watching!

 3
3