Beware of the latest malware attacks using AI and YouTube! Learn about their methods and countermeasures!

table of contents
Thank you for visiting the Beyond Blog.
is Narita work in the Marketing Department of the Technical Sales Division at Beyond Co., Ltd.
Artificial intelligence (AI) is being used in a variety of fields, and we are seeing more and more of its results in the news. While there are many benefits to AI, there have also been reports of it being used for fraud and other purposes
we will explain malware attacks that exploit YouTube , the world's most widely used online video platform
Please be extremely careful of these types of attacks
YouTube attack methods
First, here is the full modus operandi:
① Hijack a YouTube channel
② Post videos generated by AI
③ Link to the download site
④ Opening the downloaded file will result in infection
Now, let's explain each item
YouTube channel takeover
First, in order to upload videos, the YouTube channel account is hijacked using phishing scams or stealer logs
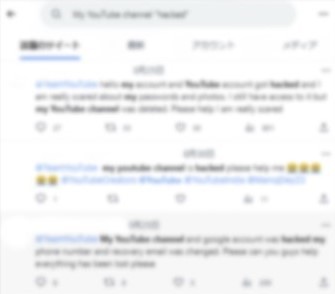
If you search for "My YouTube channel hacked" on search sites or social media, you will find many testimonials from victims
The hijacked channels range from those with 22 subscribers to those with millions of subscribers
It seems that this is not necessarily based on the number of subscribers, but the more subscribers a channel has, the stronger its spreading power and the higher its credibility, so there is a risk of creating more victims
When it comes to methods for hijacking accounts, brute force attacks and phishing scams are often used to obtain passwords and gain entry.
To address this issue, it is effective to take measures to prevent account authentication from being breached by using multi-factor authentication
Also, make sure to maintain high levels of online literacy and refrain from clicking on suspicious links or posting careless information on social media, as these could lead to your account being hijacked
Post AI-generated videos
Recently, AI tools that generate videos from text and images have emerged, making video production even easier
They are abusing this technology to create videos to upload to YouTube
The content is an explanatory video that explains how you can download pirated versions of famous paid software and apps. By choosing a popular service, your video will be more likely to be found in searches and attract more attention
The video thumbnails also use all sorts of tactics to lure users, such as featuring people extracted by AI or using popular characters
Directs you to the download site
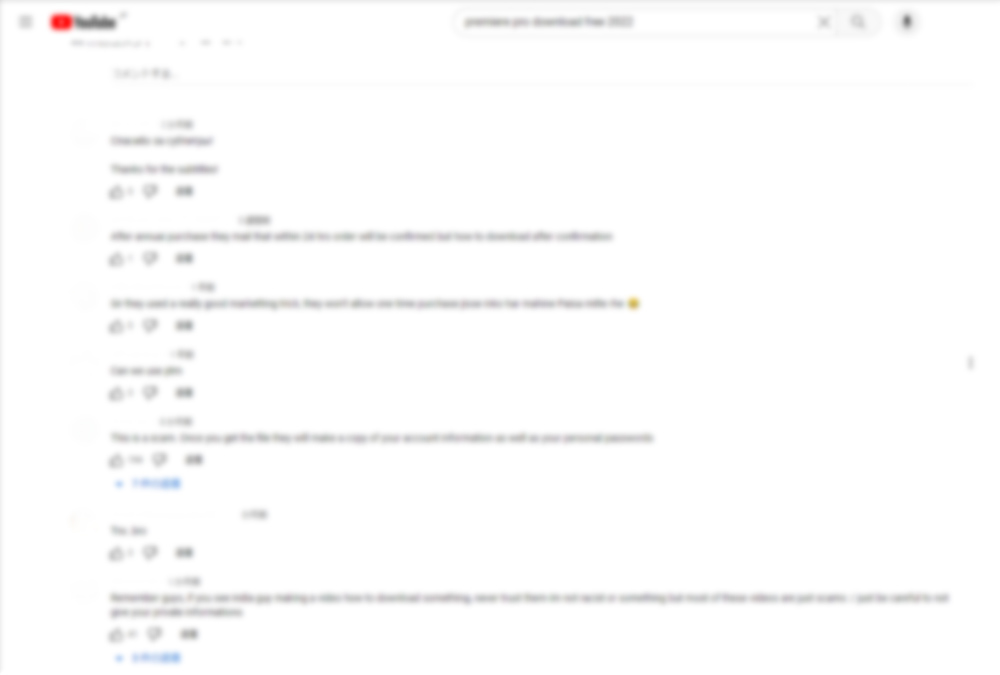
Add a URL to the description or comments section of the uploaded video, and direct users to the download site from there
In order to increase the credibility of the attached URL, several comments are posted using bots and other tools
However, if you look closely at these malicious videos, you will notice several suspicious aspects, such as duplicated comments and sentences that seem strange in Japanese
You can prevent attacks by carefully looking at the content and making a judgment without being swayed by the number of likes or comments
Run the file
When you open the downloaded file, you may be infected with ``information-stealing'' malware that extracts passwords and financial information, and recently there have been cases where ``personally identifiable information'' such as web browsing history and social media account information has been collected and transferred
A moment of carelessness online could result in real-life harm, so please be extremely careful of suspicious websites and solicitations
summary
This time, we introduced a case where AI was misused in a malware attack using YouTube videos
To avoid such problems, we strongly recommend that you download the service from the official website and not use illegal means when using the service
Thank you for watching until the end
* References *
"Increasing cyber attacks infecting people with malware using AI-generated YouTube videos" https://news.mynavi.jp/techplus/article/20230314-2624772
"Kaspersky confirms malware infection campaign on YouTube channels with over 180,000 subscribers" https://internet.watch.impress.co.jp/docs/news/1448315.html

 3
3