About the features of the cloud-based WAF "Scutum"

table of contents
This is Ohara from the Technical Sales Department
we will introduce the features of
"Scutum" that we handle *Scutum is a service provided by Secure Sky Technology Co., Ltd.
A "WAF" (Web Application Firewall) is a firewall that specializes in applications on websites
, and primarily serves to protect websites that accept input from users and
generate dynamic pages in response to requests from malicious attacks.
WAFs are unique in that they can analyze the contents of data at the application level
Cloud model (SaaS model) that changes conventional WAF concepts
Conventional WAF solutions are
provided as software that is embedded in hardware appliance servers and are designed to be operated in-house. This places
a heavy burden on engineers to maintain stable WAF operation, including the need to make complex configuration changes to servers and networks
As you can see, although the concept of WAF itself is very good,
in reality it has not become widely adopted.
Scutum is a cloud-based (SaaS) solution that overcomes the challenges of traditional WAFs.
Web application firewall functionality is provided via the Scutum Center.
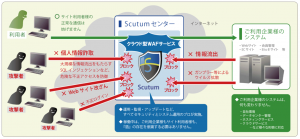
setup is completed simply by changing the DNS settings so that the IP address of your web server
It is possible to build a more secure web service environment without having to own any extra equipment
Easy to install
■ Installation in as little as 3 days
From application to start of use, you can start using the service with just a few simple procedures (in as little as three days)
■Can be installed and removed without changing the system configuration
All the customer has to do is switch the DNS, and it can be implemented immediately
■ Installation and cancellation can be done without stopping the service
There is no need to worry about website service being interrupted when installing or disabling the WAF function
FAQ
Q : When handling personal information, is it possible to encrypt communications (to prevent eavesdropping)?
A : We can handle communications encrypted using SSL.
Q : Is it possible to detect content tampering?
A : "Scutum" cannot detect content tampering, but it
be combined with a service called
"GRED" to provide a web content tampering prevention and detection service.
*However, it does not cover the recovery of tampered web content.
Q : Is it possible to detect unauthorized access?
A : It is possible to defend against the following types of external attacks.
● Defense function:
A function that blocks communication when a pre-registered fraudulent communication pattern is detected.
● Monitoring function:
A function that records communications when a pre-registered unauthorized communication pattern is detected
(the communications themselves are not blocked)
● Log function:
A function that allows you to record and view communications that appear to be fraudulent and are detected by Scutum.
● Software update function
A function to update software to improve Scutum's defense functions, etc.
● Signature update function
A function that updates malicious communication patterns to the latest version in order to improve defensive effectiveness.
● Specific URL exclusion function
A function that allows you to exclude web pages that do not require protection from the protection targets.
● Reporting and
statistical functions (attack source, attack type, action), top-level aggregation of attack source and attack type, etc.
● IP address rejection/permission function
A function to reject communication from specific IP addresses or to permit communication only from specific IP addresses.
● SSL communication function
A function that decrypts and protects encrypted communications.
Q : Is it possible to prevent unauthorized SQL statements, OS command communication, and execution (e.g., SQL injection)?
A : It is possible to detect these with the default defenses.
Q : Is it possible to detect and prevent suspicious logins?
A : We have implemented defensive signatures against brute force attacks.
Q : Do you keep logs of unauthorized access?
A : Detected logs are kept for one year.
Q : Is it possible to block communications from unexpected sources or with unexpected communication protocols?
A : It is possible to restrict access by IP address using the functions on the management screen.
*Only http(80) / https(443) are available as communication protocols.
If the origin server is configured to not accept communications other than via Scutum due to a firewall or other issue,
access to the origin server will be impossible even if you try to communicate with it using other protocols.
*By limiting the communications that the web server accepts to those that go via Scutum,
you can create a more secure environment.
Q : Is it possible to store a log of the WAF's operation status? (For understanding the operation status and reporting functions)
A : You can check the defense log from the management screen.
summary
These are the features of "Scutum"
Because it is a SaaS type, there is no need to prepare a separate appliance; the service can be started simply by changing the DNS settings
, freeing you from the hassle of managing and operating the security of your web content.
If you also want to strengthen security on the server side,
we recommend using Trend Micro's "Trend Micro Security as a Service"

 0
0






