How to "Allow security groups from other accounts" in AWS

My name is Ito and I am an infrastructure engineer
You may have multiple AWS accounts,
for various reasons, such as for internal billing purposes.
Have you ever had a situation where you wanted to separate your AWS accounts for some reason, but still wanted to communicate with them?
In the case of CIDR, if you are connecting using VPC Peering,
you can simply allow the CIDR of the opposing network.
However, since ELB does not have an internal IP address,
you will need to allow each security group.
Also, when allowing EC2 instances in an Auto Scaling group under a specific subnet,
even if individual IP addresses are allowed,
there is a possibility that the EC2 instances added by Auto Scaling will have IP addresses that are not allowed by the security group.
In such cases, you will still need to allow the security group.
So, this is how to allow "security groups of other accounts" in security groups
The image is something like this
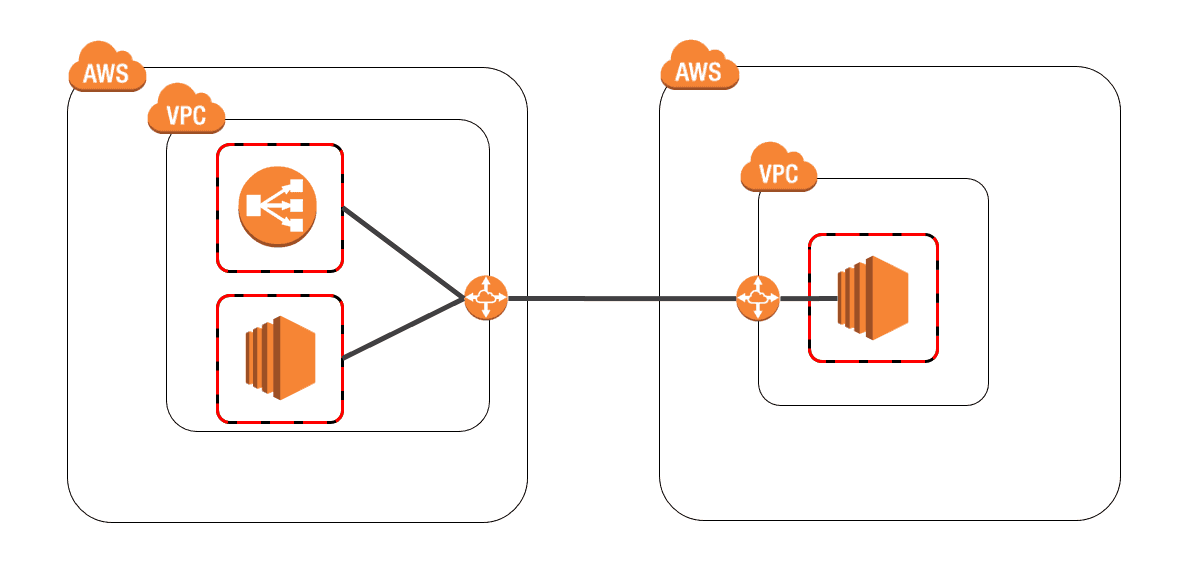
<Account ID>/<Group ID>
This is the answer.
You specify the "Account ID/Group ID" for the security group you want to allow.
You can check your account ID in the top right corner of the AWS console.
It's a 12-digit number that says "Account" in black.
You can check the group ID in the security group.
This is also mostly blacked out, but it is an ID that starts with "sg-".
By separating these two with a "/", you can allow (or deny) security groups from different accounts

It looks like this.
It's all painted black.

 1
1






