[Summary] Overview and features of Microsoft Azure [Points]

table of contents [非表示]
This is Ohara from the technical sales department.
This is a summary article of the overview, features, and points of " Microsoft Azure " (Information as of November 2017)
Overview of “Microsoft Azure”
■ Even if you create an account directly at the user company and pay, you can pay in yen instead of dollars.
(Not affected by exchange rates)
■ You can pay by bill without registering a credit card. (In this case, the free tier will disappear)
■ Even when a user company signs a contract, the governing law is Japanese law.
(Jurisdiction is Tokyo District Court)
■ There are regions in Tokyo and Osaka, so DR/BCP measures can be taken only within the domestic regions.
(By the way, AWS also plans to open an Osaka local region in 2018)
■ The SLA for each service product is guaranteed to be 99.5% or higher on a standalone level.
Obtained
CS Gold Mark Certification, a cloud security certification system based on external audits (In Japan, only two companies, Microsoft and NTT East, are certified)
■ Among cloud providers, we have the highest number of regions.
(There are 42 regions in the world)
Functional features of “Microsoft Azure”
■ Load balancer
Basic can be used for free (Standard is still a preview version)
■ Data bandwidth (data transfer amount)
/Monthly output up to 5GB is free
■ "Visual Studio" and ".NET Framework" can be used with Azure's remote desktop function.
・Applications can be developed seamlessly on Azure without the need to install a development environment.
■Azure Backup/Azure Site Recovery
- You can back up each image in a geographically distant location.
- Virtual machines are stored as VHD files, so you can back them up regularly.
LRS: Local redundancy (backup within the same region)
GRS: Geographic redundancy (backup between geographically separated regions)
[Back up virtual machines with Azure Backup]
https://docs.microsoft.com/ja-jp/azure/virtual-machines/windows/tutorial-backup-vms
- However, Azure to Azure backup is still in preview stage.
*Originally an on-premises environment → DR service on Azure
[Azure regional replication]
https://docs.microsoft.com/ja-jp/azure/site-recovery/azure-to-azure-quickstart
■ ID linkage with existing on-premises environment
- Azure Active Directory allows ID integration and management of Azure and Office 365
■ Database linkage with on-premises
・On-premises SQL Server can be failed over on Azure.
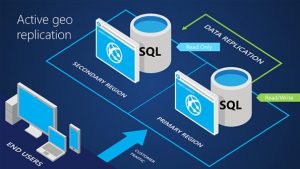
■ Active Geo Replications
A feature that allows you to create replicas in up to 4 regions
in different regions from the SQL Database running on the primary This function is mainly used as a DR/BCP countermeasure and automatically fails over.
[Reference]
https://docs.microsoft.com/ja-jp/azure/sql-database/sql-database-geo-replication-overview
*However, in the future, the RDS Availability Zone function will also be released (managed RDS)
■ Assignment of arbitrary or existing private IP address
- Can be assigned if it is a Virtual Machine.
- In the case of SQL Database,
a private IP address cannot be assigned to SQL Database in the Japan region.
*Private IP addresses can be assigned in overseas regions, but this is in preview stage.
[Reference]
https://docs.microsoft.com/ja-jp/azure/virtual-network/virtual-networks-static-private-ip-arm-pportal
*In the future,
it will be possible to directly connect to SQL Database from a virtual local network within Azure using a VPN.
*By the way, if you do not use a VPN,
SQL Database has a firewall function as standard, so you
can connect your in-house SQL Server to SQL Database using port 1433,
specify the IP address to connect, and set the security level. It is possible to increase
[Reference]
https://docs.microsoft.com/ja-jp/azure/virtual-network/virtual-network-service-endpoints-overview
■ Types of SQL Database: "Single Database" and "Elastic Pool"
・Single Database: When managing a single database
If each DB has a different purpose, launch the required number of Single Databases for each.
- Elastic pool: When managing multiple databases
Elastic pool is recommended when
multiple databases are used in a specific pattern.
For example, there is a case where each customer uses the same system, but only the database is separated.
[Reference: About elastic pool]
https://docs.microsoft.com/ja-jp/azure/sql-database/sql-database-elastic-pool
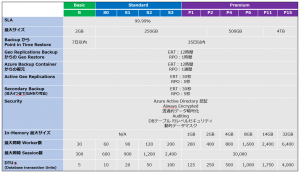
■ SQL Database service levels and specifications
・ERT: Estimated recovery time
・RPO: Recovery point objective
SQL Database security
A cloud-based directory and ID management service that supports
Azure Active Directory authentication
integrates
major directory services, advanced identity management features, and Azure AD is also a rich, standards-based platform that
allows developers to control access to their applications using centralized policies and rules
[Reference]
https://docs.microsoft.com/ja-jp/azure/active-directory/active-directory-whatis
■
Always Encrypted -
A feature designed to protect sensitive data such as credit card numbers and identification numbers stored in Azure SQL Database or SQL Server
■ Transparent Data Encryption (TDE)
- A function that encrypts stored data.
Encrypting data files in SQL Server and Azure SQL Database.
To secure your database,
you can take precautions such as designing secure systems, encrypting sensitive assets, and building a firewall on your database server.
■ SQL Database Auditing
- Tracks database events and
writes events to the audit log in your Azure storage account.
maintain and enforce regulatory compliance, understand database activity, and
gain insight into discrepancies and anomalies that indicate business concerns or suspected security violations.
[Reference]
https://docs.microsoft.com/ja-jp/azure/sql-database/sql-database-auditing
■ DB Tables Row-Level SecurityRow
allows you to control access to rows in database tables
based on the characteristics of the user performing the query (such as group membership and execution context)
[Reference]
https://docs.microsoft.com/ja-jp/sql/relational-databases/security/row-level-security
■ Dynamic Data Masking
Mask sensitive data to limit data exposure to unprivileged users.
Dynamic Data Masking (DDM)
can greatly simplify application security design and coding.
[Reference]
https://docs.microsoft.com/ja-jp/sql/relational-databases/security/dynamic-data-masking
summary
There are a lot of summaries about DB, but it seems like it can flexibly respond to DB requirements, so
it might be a good idea as a DR/BCP measure for core business systems.

![[Compatible with over 200 countries] Global eSIM “Beyond SIM”](https://beyondjapan.com/cms/wp-content/uploads/2024/05/beyond_esim_blog_slider1-768x345.jpg)
![[If you are traveling, business trip, or stationed in China] Chinese SIM service “Choco SIM”](https://beyondjapan.com/cms/wp-content/uploads/2024/05/china-sim_blogbanner-768x345.jpg)
![[Global exclusive service] Beyond's MSP in North America and China](https://beyondjapan.com/cms/wp-content/uploads/2024/06/gloval_surport_blog_slider-768x345.jpg)
![[YouTube] Beyond official channel “Biyomaru Channel”](https://beyondjapan.com/cms/wp-content/uploads/2021/07/バナー1-768x339.jpg)
![[Osaka/Yokohama/Tokushima] Looking for infrastructure/server side engineers!](https://beyondjapan.com/cms/wp-content/uploads/2022/12/recruit_blog_banner-768x344.jpg)
![[Deployed by over 500 companies] AWS construction, operation, maintenance, and monitoring services](https://beyondjapan.com/cms/wp-content/uploads/2021/03/AWS_構築・運用保守-768x344.png)
![[Successor to CentOS] AlmaLinux OS server construction/migration service](https://beyondjapan.com/cms/wp-content/uploads/2023/08/almalinux_blogbanner-768x344.png)
![[For WordPress only] Cloud server “Web Speed”](https://beyondjapan.com/cms/wp-content/uploads/2022/11/webspeed_blog_banner-768x344.png)
![[Cheap] Website security automatic diagnosis “Quick Scanner”](https://beyondjapan.com/cms/wp-content/uploads/2023/04/quick_eyecatch_blogbanner-768x345.jpg)
![[Reservation system development] EDISONE customization development service](https://beyondjapan.com/cms/wp-content/uploads/2023/06/edisone_blog_banner-768x345.jpg)
![[Registration of 100 URLs is 0 yen] Website monitoring service “Appmill”](https://beyondjapan.com/cms/wp-content/uploads/2021/03/Appmill_ブログバナー-768x344.png)
 0
0
![[2025.6.30 Amazon Linux 2 support ended] Amazon Linux server migration solution](https://beyondjapan.com/cms/wp-content/uploads/2024/05/59b34db220409b6211b90ac6a7729303-1024x444.png)