Kaspersky released an open-source antivirus tool, so I tried it out (Kaspersky Virus Removal Tool for Linux)

table of contents
Hello.
from the Memory Exhaustion
System Solutions Department.
Recently I was looking for a good open-source antivirus software product, and I
Kaspersky Virus Removal Tool for Linux the famous Kaspersky company released around June, which caught my eye, so I decided to write an article about it as a memo after briefly testing it.
download
■ Verification environment
Ubuntu 24.04 LTS Kaspersky Virus Removal Tool 24.0.5.0
Let's try downloading it from the link below:
https://www.kaspersky.com/downloads/free-virus-removal-tool
Basically, you can follow the official instructions.
It's convenient because you don't need to install it each time you run it.
https://support.kaspersky.com/help/kvrt/2024/en-us/269465.htm
After downloading it from the browser, change the permissions and run it.
First, run it from the GUI.
$ cd ~/Downloads $ chmod +x kvrt.run $ ./kvrt.run Running with root privileges Generated directory is</tmp/9d208c686fe9d56312596> Verifying archive integrity... 100% SHA256 checksums are OK. All good. Uncompressing Kaspersky Virus Removal Tool 24.0.5.0 for Linux 100% ================================= Running kvrt with args <> ================================= compver: 24.0.5.0 x86-64 (Jul 9 2024 17:36:48) Product folder ----------------------------
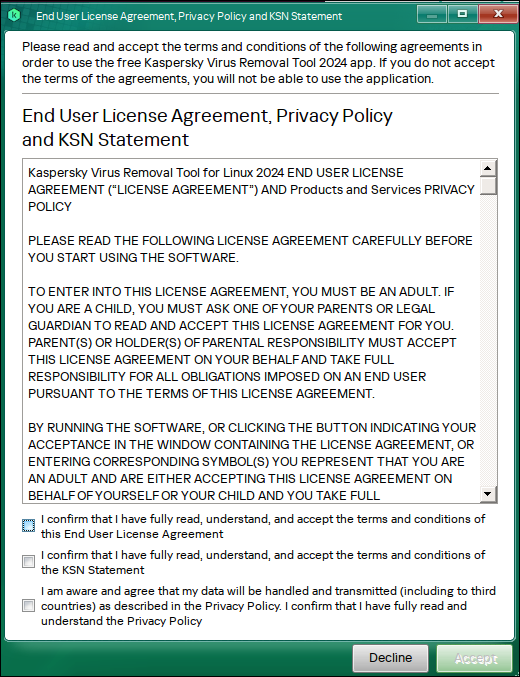
▼ The terms of use will be displayed. If you can confirm each one, check the box and proceed to the next step
▼ The first time you install it, version information will be displayed. Once you have confirmed it, press Close and then click [Start Scan]
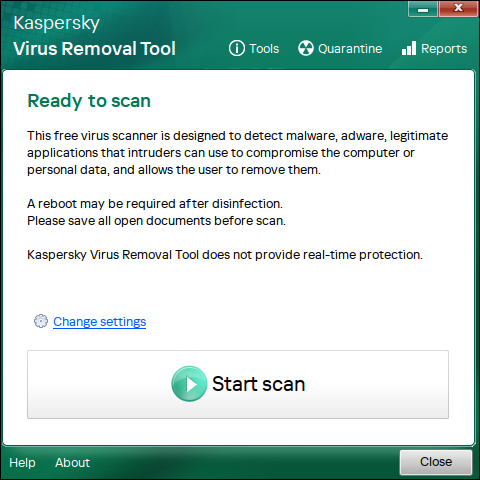
▼ Wait for the scan to run. Since I ran it on a clean image this time, nothing was detected
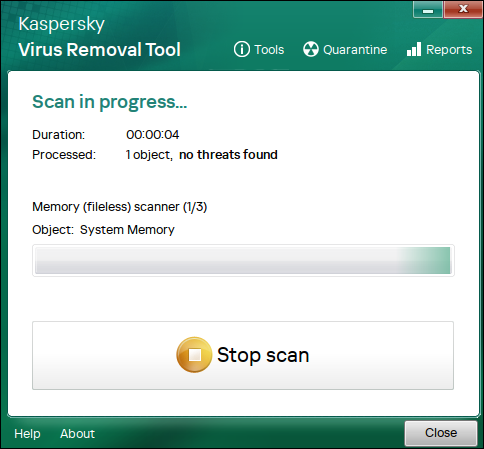
This tool can only be run on an ad-hoc basis and does not have a real-time scanning function.
If you run it manually, the GUI is fine, but if you want to run it periodically, it is recommended that you add it to a cron and run it via CLI.
Next I'll try it via the CLI
Via CLI
First, get help:
https://support.kaspersky.com/help/kvrt/2024/en-us/269475.htm
-h - show help -d<folder_path> - path to quarantine and reports folder -accepteula - accept EULA, Privacy Policy and KSN Statement -trace - enable trace collection -tracelevel<level> - set the level of traces: ERR - only error messages WRN - warnings and errors INF - information, warnings and errors DBG - all messages -processlevel<level> - set the level of danger of object which will be neutralized: 0 - skip objects with high, medium and low danger level 1 - neutralize objects with high danger level 2 - neutralize objects with high and medium danger level 3 - neutralize objects with high, medium and low danger level -dontencrypt - disable encryption of trace files/reports/dump files -details - enable detailed reports -proxyconfig<config_file_path> - path to file with proxy config -silent - run scan without GUI -adinsilent - run active disinfection in silent mode -allvolumes - add all volumes to scan -custom<folder_path> -path to custom folder for scan -customlist<file_path> -path to file with custom folders for scan -exclude<folder_path> -exclude path from custom scan -excludelist<file_path> - path to file with excludes for custom scan -customonly - run scan of custom folders only
I'll try running it with the minimum options
-silent will not start the GUI,
-accepteula will skip the terms and conditions.
$ ./kvrt.run -- -silent -accepteula Graphical mode is<wayland> localuser:root being added to access control list Running with root privileges Generated directory is</tmp/92302b5bca4f82e716374> Verifying archive integrity... 100% SHA256 checksums are OK. All good. Uncompressing Kaspersky Virus Removal Tool 24.0.5.0 for Linux 100% ================================= Running kvrt with args <-trace -silent -accepteula> ================================= compver: 24.0.5.0 x86-64 (Jul 9 2024 17:36:48) Product folder ================================== Scan is started =================================================================== Scan is finished with results: Processed: 27957 Processing errors: 0 Detected: 0 Password protected: 0 Corrupted: 0 ================================== ================================== kvrt exited with code <0> ================================= localuser:root being removed from access control list
As with the GUI, nothing was detected
Try to detect malware
Next, we will try to detect malware.
As a preliminary step, download the file from the eicar website below (under ./Downloads):
https://www.eicar.org/download-anti-malware-testfile/
▼ Place the eicar file under Downloads
$ ls -l total 151296 -rw-rw-r-- 1 hamchan hamchan 68 Oct 29 10:26 eicar.com -rw-rw-r-- 1 hamchan hamchan 184 Oct 28 14:01 eicar_com.zip
This time, I will try running it by specifying it under Downloads
-trace Enables tracing.
-tracelevel Set to "DEBUG" to output all event logs.
-custom Specify the inspection directory.
-processlevel Set to 3 this time to detect all threats in the low to high range.
./kvrt.run -- -accepteula -trace -tracelevel DBG -custom /home/hamchan/Downloads/ -processlevel 3 -silent Graphical mode is<wayland> localuser:root being added to access control list Running with root privileges Generated directory is</tmp/74a8bcf3a3339fc810150> Verifying archive integrity... 100% SHA256 checksums are OK. All good. Uncompressing Kaspersky Virus Removal Tool 24.0.5.0 for Linux 100% ================================== Running kvrt with args <-accepteula -trace -tracelevel DBG -custom /home/hamchan/Downloads/ -processlevel 3 -silent> ================================= compver: 24.0.5.0 x86-64 (Jul 9 2024 17:36:48) Product folder ================================== Scan is started ================================== Threat<EICAR-Test-File> is detected on object</home/hamchan/Downloads/eicar.com> Threat<EICAR-Test-File> is detected on object</home/hamchan/Downloads/eicar_com.zip> ================================= Scan is finished with results: Processed: 27961 Processing errors: 0 Detected: 2 Password protected: 0 Corrupted: 0 ================================= Action<Cure> is selected for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar.com> Action<Cure> is selected for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar_com.zip> ================================= Disinfection is started ================================= Disinfection action<Quarantine> for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar.com> is finished with status<Quarantined> Disinfection action<Quarantine> for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar_com.zip> is finished with status<Quarantined> Disinfection action<Cure> for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar.com> is finished with status<CureFailed> Disinfection action<Cure> for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar_com.zip> is finished with status<CureFailed> Disinfection action<Delete> for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar.com> is finished with status<Deleted> Disinfection action<Delete> for threat<EICAR-Test-File> on object</home/hamchan/Downloads/eicar_com.zip> is finished with status<Deleted> ================================= Disinfection is finished with results: Processed: 4 Processing errors: 0 Skipped: 0 Quarantined: 2 Quarantine failed: 0 Cured: 0 Cure failed: 2 Cure on reboot: 0 Deleted: 2 Delete on reboot: 0 Restored: 0 Restore on reboot: 0 ================================== ================================== kvrt exited with code <0> ================================= localuser:root being removed from access control list
Judging from the log, it seems that the detection was successful, and the file was deleted after being quarantined.
The file has also disappeared from the directory.
$ ls -lha drwxr-xr-x 2 hamchan hamchan 4.0K Oct 29 10:49 . drwxr-x--- 17 hamchan hamchan 4.0K Oct 29 10:44 ..
By the way, quarantined files are saved to the following location each time the command is executed (when executed as root)
$ sudo ls -l /var/opt/KVRT2024_Data total 24 drwx------ 2 root root 4096 Oct 28 13:52 Anomalies drwx------ 2 root root 4096 Oct 29 10:45 'Legal notices' drwx------ 4 root root 4096 Oct 29 10:49 Quarantine drwx------ 2 root root 4096 Oct 29 10:45 Reports drwx------ 2 root root 4096 Oct 29 10:49 Temp drwx------ 2 root root 4096 Oct 29 10:45 Traces $ sudo ls -l /var/opt/KVRT2024_Data/Quarantine total 12 drwx------ 2 root root 4096 Oct 29 10:49 KVRTQ0001 drwx------ 2 root root 4096 Oct 29 11:34 KVRTQ0002 drwx------ 2 root root 4096 Oct 29 11:41 KVRTQ0003
If you want to restore a file due to a false detection, etc., you can do so via the GUI.
https://support.kaspersky.com/help/kvrt/2024/en-us/269476.htm
▼ If you select a file from the list and restore it, the file will be restored to its original directory.
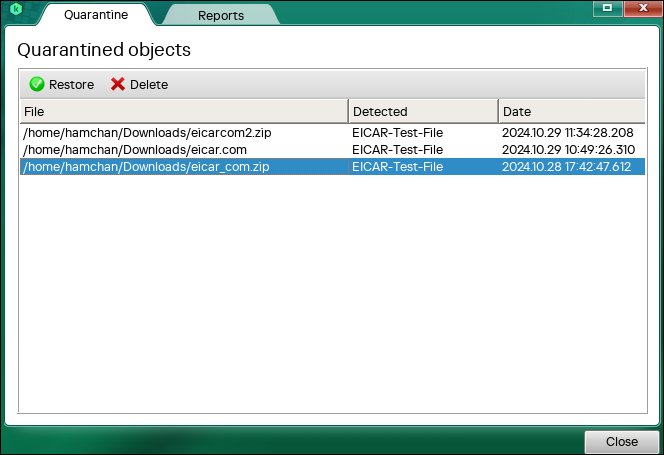
Although it is simpler than paid software, it
is open source and can do so much, and it is relatively lightweight, so I think it might be quite viable for personal use.
Microsoft has also recently released a tool for Linux, so I would like to test it out again when I have time.
complete

 12
12






