Is your VPN connection really secure?

table of contents
Hello,
my table when I work from home is a box of Ehime mandarin oranges 🍊
This is Kawai from the System Solutions Department.
We're slowly starting to feel the winter coming.
I, too, tend to work remotely and stay at home on cold or bad weather days.
While there is a trend to return to the basics of going to the office, I think there are still many companies that have introduced or promoted remote work since the COVID-19 pandemic.
As a result, the use of remote access VPNs from home has also increased, but is it really safe to operate them?
In this article, I would like to write about the mechanism and challenges of remote access VPNs
Advantages and Disadvantages of Remote Access VPN
First, let's organize the basic advantages and disadvantages of remote access VPNs
The main purpose of a remote access VPN is to securely connect to the office from home or on the go .
Secondly, when connecting to public Wi-Fi in a cafe or other location, it can be used to ensure security when connecting to insecure wireless standards such as WPA (although ideally you would not want to connect in the first place ...).
( There are also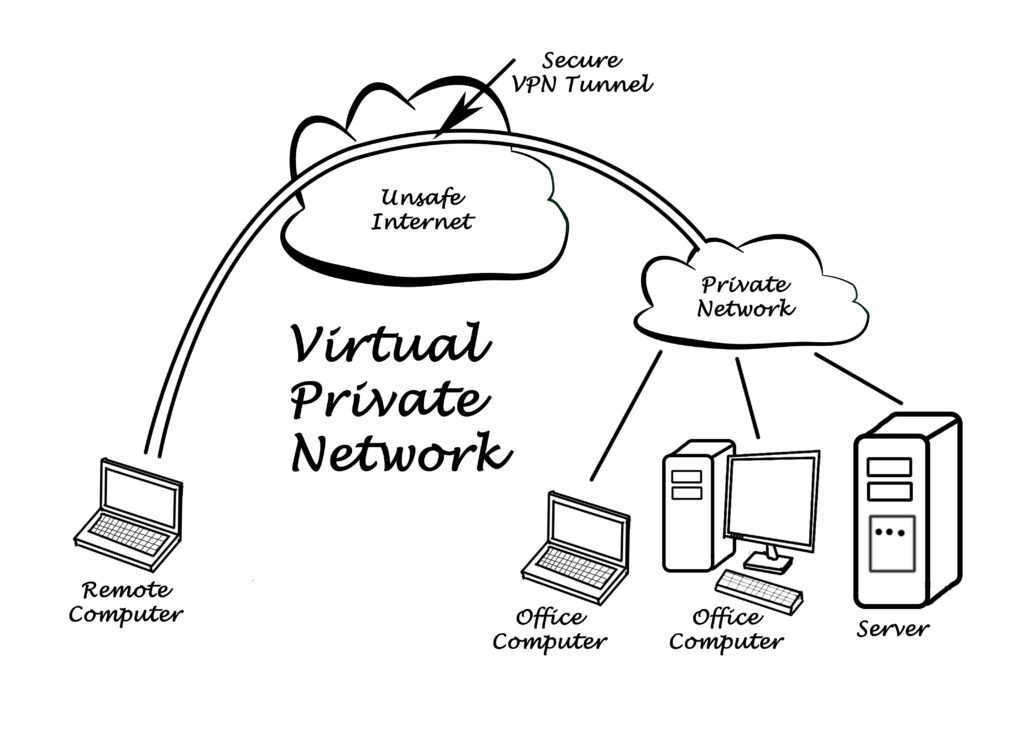 Evil Twins attacks *For more information on the types of protocols used in wireless connections, see the following Kaspersky article, which is concise and detailed
Evil Twins attacks *For more information on the types of protocols used in wireless connections, see the following Kaspersky article, which is concise and detailed
: https://www.kaspersky.co.jp/resource-center/definitions/wep-vs-wpa
The
main benefit is data
encryption With a VPN, even when using a public network such as a cafe, communication to the VPN server (such as a company router) is encrypted, reducing the risk of interception.
As mentioned above, securely access local file servers and internal systems located within the office , allowing you to obtain information necessary for work from virtually anywhere.
by configuring routing, you can connect from outside to an IP-restricted environment using the office IP as the source (a so-called zero route). Very convenient.
■Disadvantages
However, one disadvantage to keep in mind that even if you connect to a VPN, not everything will be safe .
On the flip side of this advantage, a VPN only encrypts the route from home to work .
If your access to the internet beyond that point is not encrypted separately using HTTPS or similar, security will not be ensured even if you use a VPN.
There are also concerns about communication speed and connection stability.
VPN connections encrypt communications and bypass routes, which can make connections more unstable than usual .
The additional process of decrypting and re-encrypting encrypted packets increases the load on the router that acts as the VPN server, and in some cases can affect the local Internet connection.
How remote access VPNs work and what types are there?
There are several remote access VPN methods, each with its own advantages and disadvantages.
In this section, we will briefly introduce the most commonly used methods.
(Each method name is hyperlinked to an article by "SE no Michishiru" (SE Guidepost). Please refer to it for more information.)

[
IPsec/L2TP ] IPsec (Security Architecture for Internet Protocol or Internet Protocol Security) is a protocol that authenticates and encrypts data packets and is used in combination with L2TP (Layer 2 Tunneling Protocol).
Authentication method: Pre-shared key or certificate.
Advantages: Provides high security and is supported as standard by many operating systems.
Disadvantages: Encryption processing is limited to connections in NAT environments, so configuration may be difficult depending on the environment.
It first encapsulates packets using L2TP and tunnels them through the data link layer.
L2TP does not have encryption capabilities and does not provide sufficient security on its own, so confidentiality and integrity are ensured by protecting these packets with IPsec, and encryption and authentication are provided using IP protocols such as AH and ESP.
[
SSL VPN ] SSL VPN is a method of creating a VPN tunnel using HTTPS.
It can be accessed from a web browser and encrypts data using the SSL/TLS protocol.
Authentication methods: ID/password, one-time password, certificate, etc.
Advantages: Works with a standard web browser, making it easy to connect even in a NAT environment.
Disadvantages: Dependence on web traffic means that compatible applications are (sometimes) limited.
It is simple because TCP/443 can generally be used. Also, compared to IPsec/L2TP, there is less processing required and communication speeds can be expected to be stable.
Please note that if there is overlap with other services, the port number must be shifted.
[
IKEv2 ] IKEv2, when combined with IPsec, provides a VPN that is particularly suited to mobile environments.
Authentication method: Certificate authentication, EAP (Extensible Authentication Protocol)
Advantages: Connections can be re-established quickly and are strong even when moving.
Disadvantages: Compared to other methods, many devices do not support it.
Is VPN really safe? - Considering the concept of defense in depth

That was a long introduction, but now we come to the main part
VPNs are one option for strengthening remote access security, but of course they do not provide complete defense on their own.
To protect important data and systems, a multi-layered, multi-stage defense incorporating the concept of zero trust is necessary.
■Newly discovered vulnerability (CVE-2024-3661)
Around May 2024, an attack method was reported that poisons routing tables even under a VPN connection, preventing communications from going through the tunnel.
Details: https://jvn.jp/ta/JVNTA94876636/This
method uses DHCP option 121, and although the attacker needs to have a malicious DHCP server within the network, it
has become a hot topic as an attack method that threatens intranets that had previously been thought to be secure.
■An actual case where VPN equipment became an entry point
Another recent example is the incident at the Osaka General Medical Center in 2022. caused
the hospital's systems to stop working, requiring all operations to be handled manually, and it took about a year for full recovery.
According to the investigation report, https://www.gh.opho.jp/pdf/report_v01.pdf
The intrusion route in this case was a supply chain attack via Company E's food service center.
The firmware for Firewall Z, which was the intrusion route, had not been updated, and it was confirmed
enabled constant RDP communication (port number: 3389) from Company E's information system on Firewall Y, but subsequently failed to check or improve the operational status
The above is a quote from "4.2.3. Summary of Technical Causes" in the report, but this case shows that headquarters are not the only point of entry.
Cases of so-called supply chain attacks, where an attacker infiltrates through VPN devices at branch offices or affiliated companies and then spreads to headquarters via a closed network, are common.
This highlights the that no matter how well you secure the entry point, intranets are extremely vulnerable once infiltrated .
Therefore, even if communications are encrypted using a remote access VPN, if the connecting client is already infected, the VPN is useless.
■The concept of zero trustZero
trust is based on the principle of "no trust" and is a concept that verifies and authenticates all communications, devices, and users that access the network (evil nature theory).
Risks are minimized by combining VPN connections, access control, confirmation of communication content, and two-factor authentication.
A specific solution is to utilize authentication services such as Azure Active Directory (Azure AD).
Using Azure AD, you can set authentication policies for each user's device/application, allowing for detailed control of access from outside the company.
For details: https://learn.microsoft.com/ja-jp/azure/security/fundamentals/zero-trust
No matter how much protection you provide for authentication and pre-processing, in addition to
endpoint defense and detection Therefore, in preparation for the unlikely event of an intrusion or infection, it has become almost essential
to collect and monitor logs using asset management software, etc., and to implement endpoint security products *An overview of endpoint security has been introduced in a previous article▼
・Easy-to-understand explanation of endpoint security
summary
VPNs are certainly convenient and powerful, but it's dangerous to think that "just because I'm using a VPN, I'm safe."
Remote access VPNs only encrypt communications from your home to the company router, but do not protect internet communications beyond that.
To ensure adequate security, it's important to have a flexible design that incorporates a multi-layered defense approach, zero trust, and an authentication infrastructure.
Incidentally, one interesting development is that Microsoft published
stating that they will deprecate PPTP and L2TP methods in the future *PPTP is too vulnerable to begin with, so it is better not to use it.
In the future, there may be a trend towards migrating to SSTP, which is not mentioned in this article, and the aforementioned IKEv2.
https://techcommunity.microsoft.com/blog/windowsservernewsandbestpractices/pptp-and-l2tp-deprecation-a-new-era-of-secure-connectivity/4263956
https://ascii.jp/elem/000/004/227/4227428/#:~:text=%E3%83%9E%E3%82%A4%E3%82%AF%E3%83%AD%E3%82%BD%E3%83%95%E3%83%88%E3%81%AF%E3%80%812024%E5%B9%B410,%E3%82%92%E6%8E%A8%E5%A5%A8%E3%81%97%E3%81%A6%E3%81%84%E3%81%8F%E3%80%82
complete

 8
8






