Improve your security in just 5 minutes! Set up two-factor authentication
table of contents
Morita from the Technical Sales Department .
Leaks of email addresses and passwords from large-scale services happen frequently.
Many people may remember recent incidents such as the Japan Pension Service and Yahoo! JAPAN.
There are quite a few
major personal information leak cases listed on Wikipedia It's a scary world we live in...
No matter how trustworthy a company is, it is extremely difficult to guarantee 100% security, and there is a limit to what individuals can do to prevent data leaks
However, even if your email address or password is stolen, there is a way to prevent unauthorized use of your account.
That is two-factor authentication, which we will introduce here.
table of contents
- What is two-factor authentication?
- What services support two-factor authentication?
- All the basics: Setting up Google Authenticator
- Other two-factor authentication apps
- summary
◆What is two-step authentication?
This is a system that authenticates your identity by going through a two-step process when using a service
include
passwords set by users
and one-time passwords issued by tokens used in online banking
In addition, the Google authentication system we will introduce this time
uses a password (something the user knows)
and a smartphone (something the user has)
Other similar terms include two-way authentication, two-factor authentication, and multi-factor authentication, but we will not explain them here
What services support two-step authentication?
Many services that you may use for work or personal purposes support this feature. If you use these services, we recommend that you set up two-factor authentication
- Amazon
- Amazon Web Services
- Backlog
- Dropbox
- Evernote
- GitHub
- Google Account
- Google Apps for Work
- Microsoft account
- Slack *Installation instructions have been published
- Tumblr
- WordPress.com
*We plan to add instructions on how to set up each service in the future
As of March 23, 2017, it's unfortunate that ChatWork, which we use at our company, is not yet supported..
Development of new features and improvements
ChatWork Ver. 4.0 is planned for this year, and the following features are currently under development:
Complete renewal of mobile apps (iOS, Android) Enhanced
task and video conferencing functions
Introduction of two-step authentication
desktop app
API
Improved response, more stable operation
Strengthened response to user feedback
ChatWork Opinions and Requests Forum
(There are also various other features under development that we cannot announce yet.)
Monday, April 27, 2015 ChatWork moves to the next stage - Funding announcement from GMO VP
There is an article about this, but...
Chatwork, we look forward to adding more features!
◆ All the basics: Setting up Google Authenticator
Now, let's set up Google two-step authentication, which serves as the basis for authenticating various services
First, open
Google 2-Step Verification and click "Try it" in the top right corner.
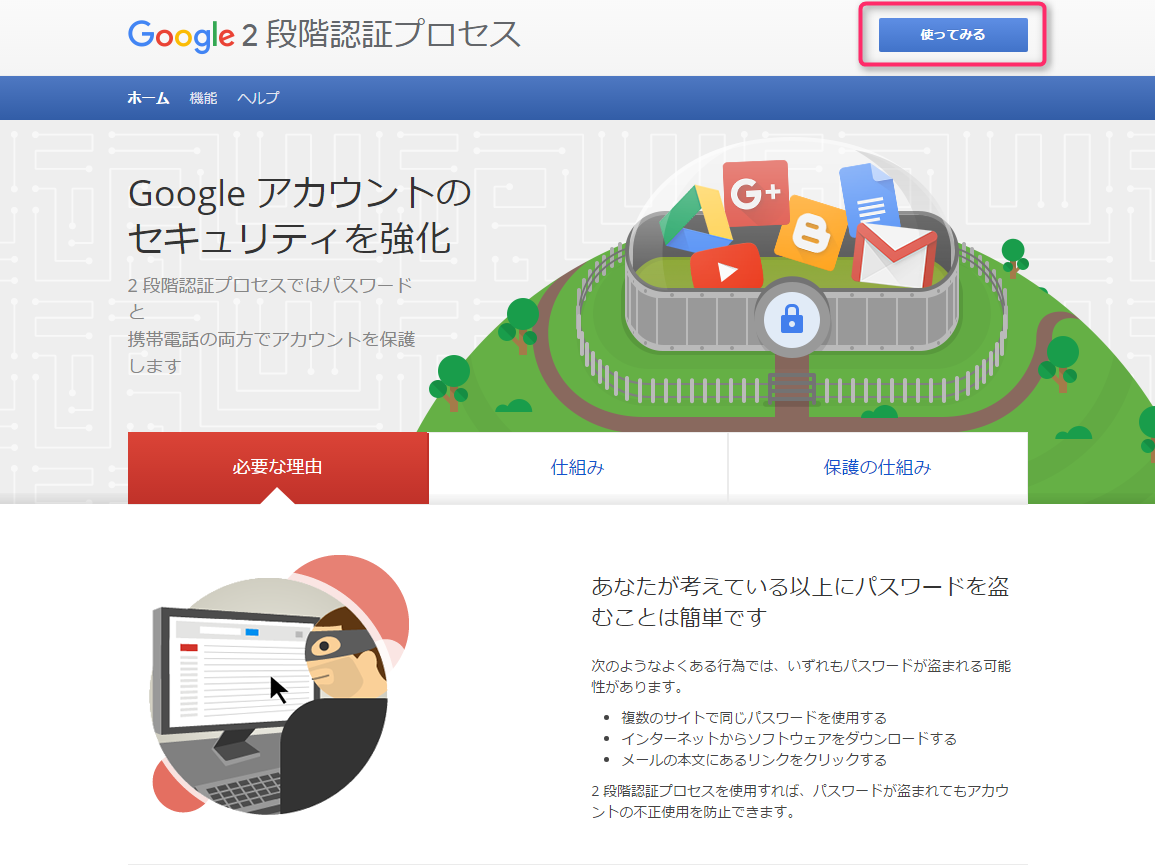
Click "Start" at the bottom right
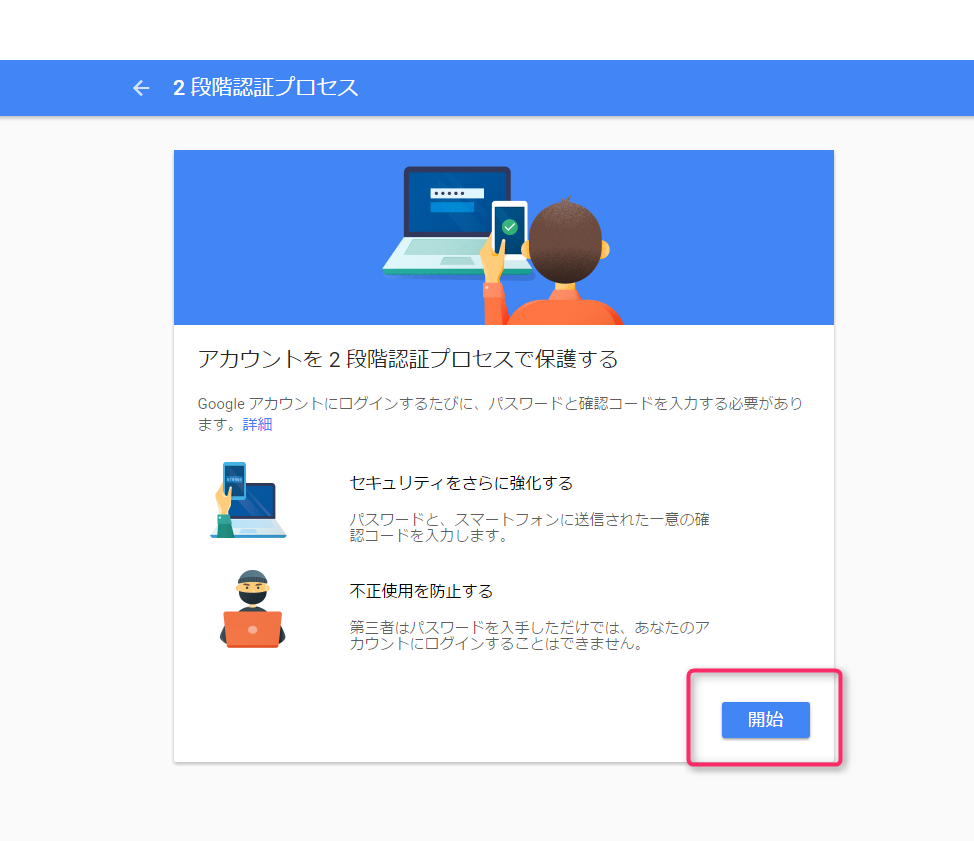
Enter your mobile phone number after "+81" without the first "0".
This time, select "Text Message" and click "Next".
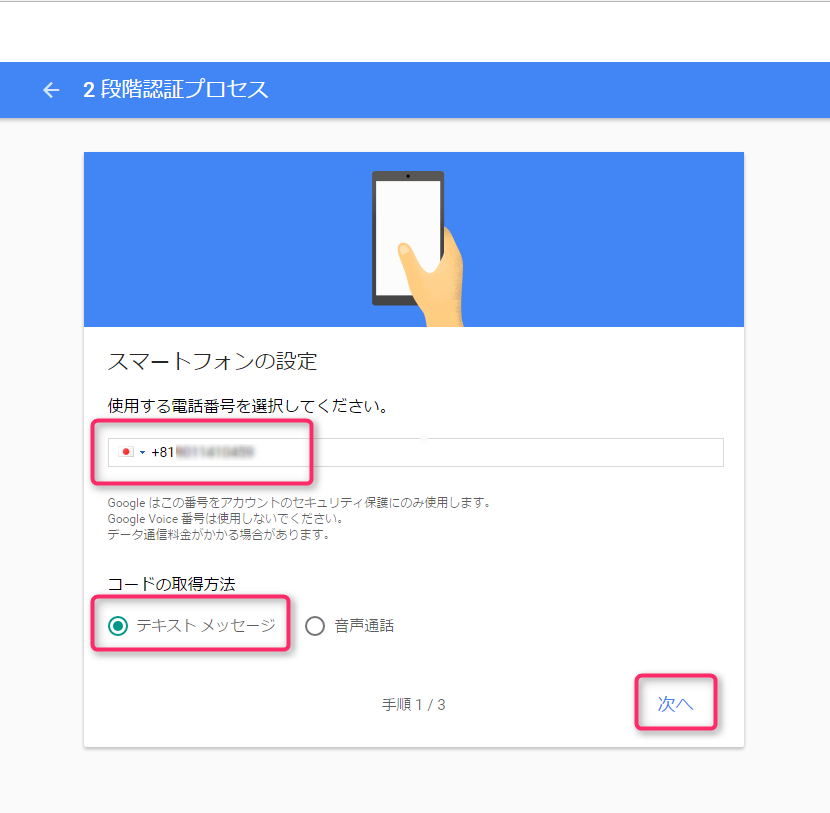
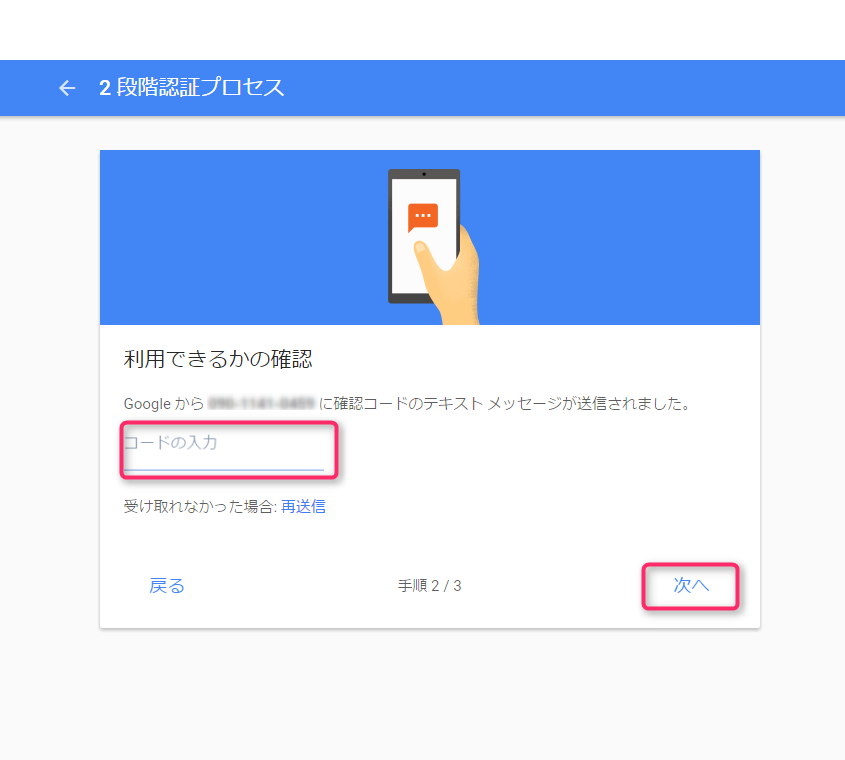
A code will be sent from Google to the mobile phone number you entered above.
Enter the code and click "Next."
Click "Turn On"
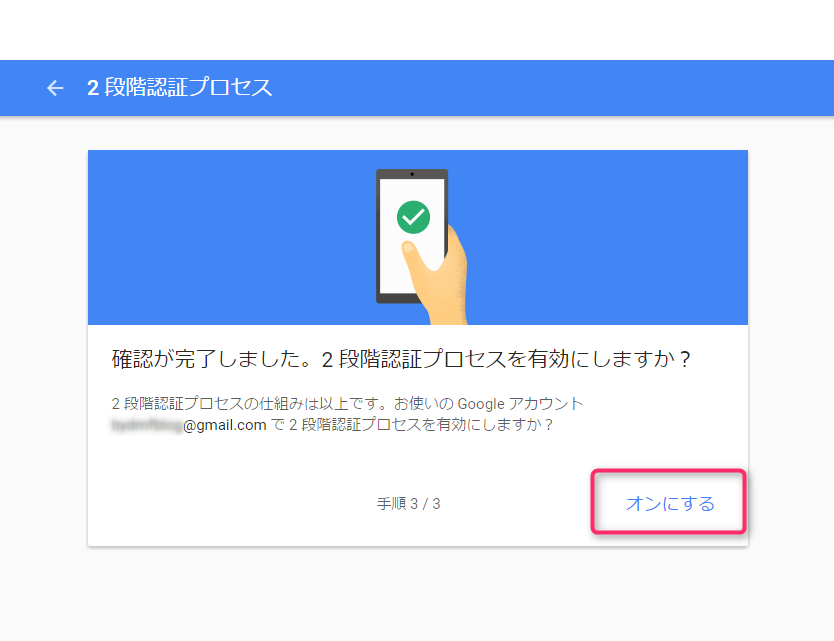
Now the two-step verification process is enabled. It's super easy
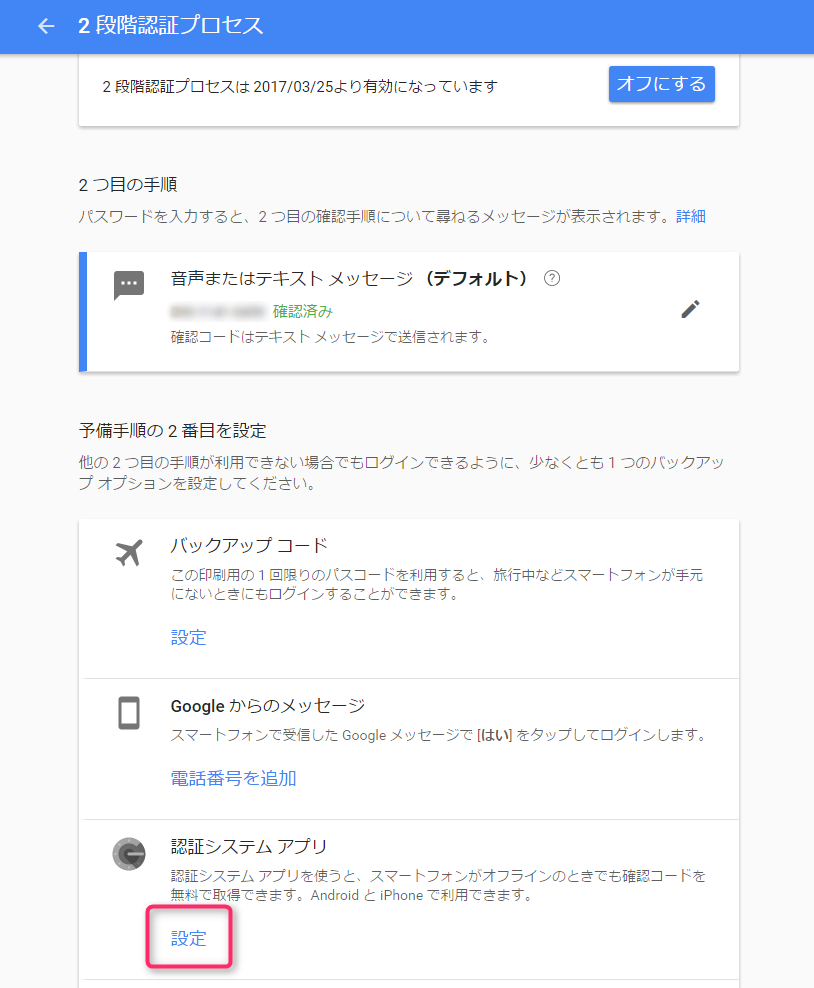
Next, let's set up the Google authentication system app "Authenticator."
Scroll down a little and click "Settings" under "Authentication System App."
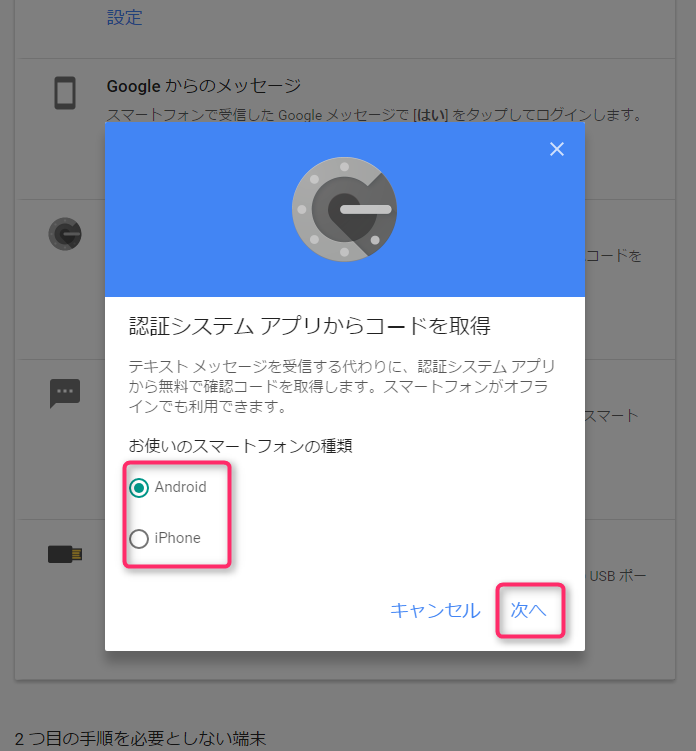
Enter the type of smartphone you are using.
In this example, we selected Android.
A code will be sent from Google to the mobile phone number you entered above.
Enter the code and click "Done."
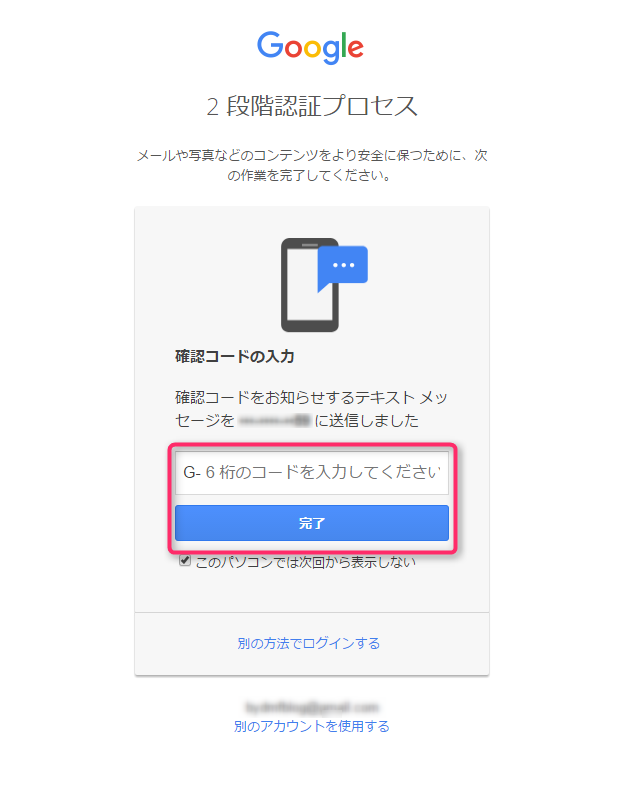
Then, click "Settings" in the "Authentication System App" again and enter the type of smartphone you are using
Google Authenticator to your smartphone and launch it.
After launching the app, tap the "+" button in the top right corner of the screen, then tap "Scan barcode" at the bottom of the screen. Scan
the QR code shown on the screen below.
After that, "google" will be added to the app and a 6-digit code will be displayed.
Return to the computer screen and click "Next."
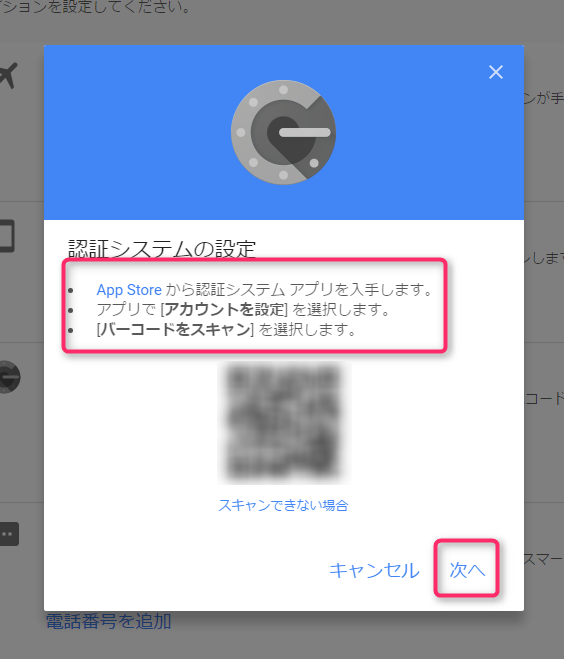
Enter the code displayed in the app and click "Confirm."
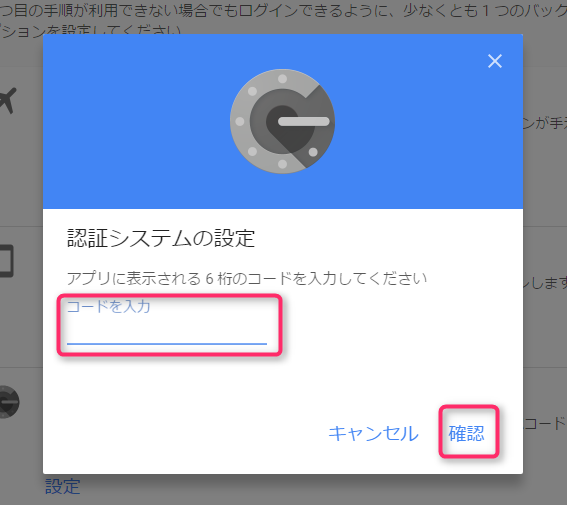
Finally, click "Done" to complete the Google Authenticator setup
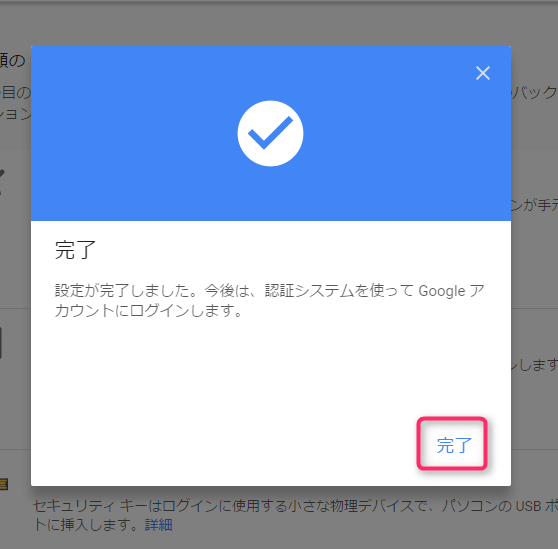
◆Other two-factor authentication apps
In addition to the Google Authenticator introduced here, other apps that can be used for two-step authentication include:
In Japan, IIJ SmartKey is also widely used
Summary
Why not take this opportunity to reassess your account management?
In addition to setting up the two-step authentication mentioned above, we would like you to reconsider your username and password management policies
For example,
do not use the same password on multiple sites
, do not use passwords that are easy to guess
, use an automatic password generation tool
, and change your password regularly
.
keepass that can conveniently solve this problem , so please try it out if you are interested. I would like to summarize some useful ways to use keepass in the future.

 0
0






